Global 5G Security Market Size, Share, Industry Analysis Report By Offering (Solutions (Next-Generation Firewall, Data Loss Prevention, Antivirus/Antimalware, Distributed Denial of Service Protection, Security Gateway, Sandboxing, Others), Services (Consulting, Implementation, Support & Maintenance), By Network Component Security (Radio Access Network Security, Mobile Core Security), By Architecture (5G NR Standalone, 5G NR Non-Standalone), By End-User (Telecom Operators, Enterprises), By Application (Virtual & Augmented Reality, Connected Automotive, Smart Manufacturing, Wireless EHealth, Smart Cities, Others), By Vertical (Manufacturing, Healthcare, Energy & Utilities, Retail, Automotive & Transportation, Public Safety, Media & Entertainment, Others.), By Regional Analysis, Global Trends and Opportunity, Future Outlook By 2025-2034
- Published date: Oct. 2025
- Report ID: 121380
- Number of Pages: 198
- Format:
-
keyboard_arrow_up
Quick Navigation
- Report Overview
- Key Takeaways
- Key 5G Cyberthreat Statistics
- Role of Generative AI
- Regional Insight: Asia-Pacific and China
- Emerging Trends in 5G Security
- Growth Factors
- By Offering
- By Network Component Security
- By Architecture
- By End User
- By Application
- Key Market Segments
- Drivers
- Restraints
- Opportunities
- Challenges
- Key Players Analysis
- Recent Developments
- Report Scope
Report Overview
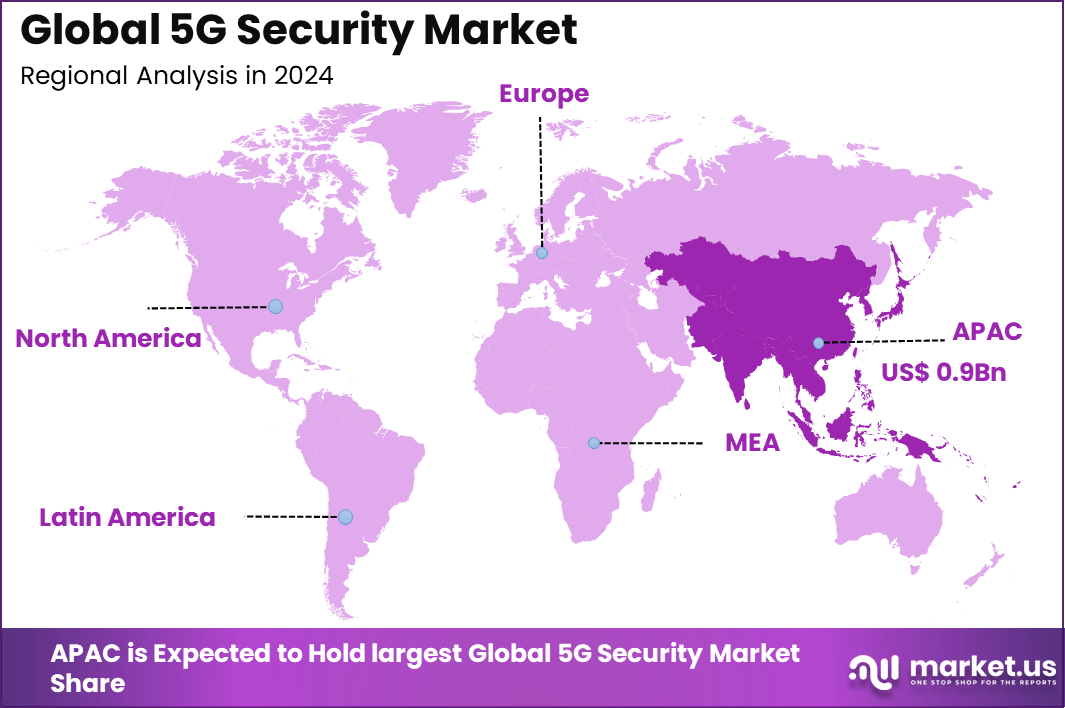
The Global 5G Security Market generated USD 2.6 billion in 2024 and is predicted to register growth from USD 3.5 billion in 2025 to about USD 53.9 billion by 2034, recording a CAGR of 35.3% throughout the forecast span. In 2024, APAC held a dominan market position, capturing more than a 38.4% share, holding USD 0.9 Billion revenue.
The 5G security market refers to solutions and services designed to protect fifth-generation mobile networks, their infrastructure, and connected devices from cyber threats, unauthorized access, data breaches, and disruption. These cover network security, endpoint security, application and device security, and services such as consulting and managed security.
Top driving factors for the 5G Security Market center on the surge in cyber threats targeting 5G networks and the increase in connected IoT devices. As the number of connected devices grows beyond billions, so does the attack surface, creating urgent demand for robust security measures. Another key driver is the regulatory push from governments enforcing stricter cybersecurity standards to safeguard critical infrastructure.
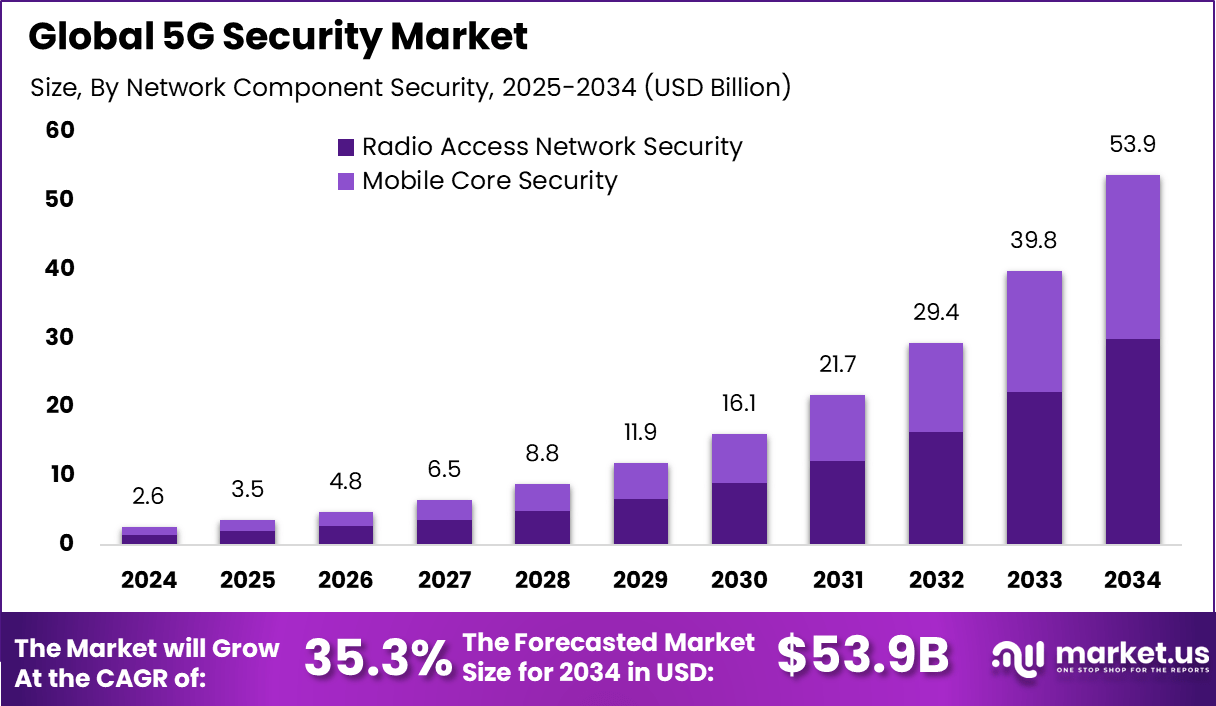
The substantial growth in sectors reliant on real-time data and connectivity. The telecommunications sector leads with more than 60% share, driven by network operators deploying secure 5G infrastructure. Healthcare and manufacturing also exhibit strong demand due to critical data handling and automation needs. Cloud deployment of security solutions is growing rapidly, reflecting the shift to scalable, flexible security that can keep pace with evolving threats.
Increasing adoption technologies in 5G security include zero-trust architecture, AI/ML-based analytics, and network slicing with dedicated security policies for different slices. Zero-trust models improve security by limiting access privileges unless explicitly granted, which is crucial as IoT ecosystems expand. AI technologies allow for swift identification of anomalies in massive data flows, preventing attacks before damage occurs.
Key Takeaways
- The Solutions segment dominated with 65.4%, reflecting strong enterprise demand for integrated security platforms to safeguard next-generation 5G networks.
- Radio Access Network (RAN) Security led with 55.7%, driven by the need to protect edge connections and prevent network intrusion in multi-vendor 5G environments.
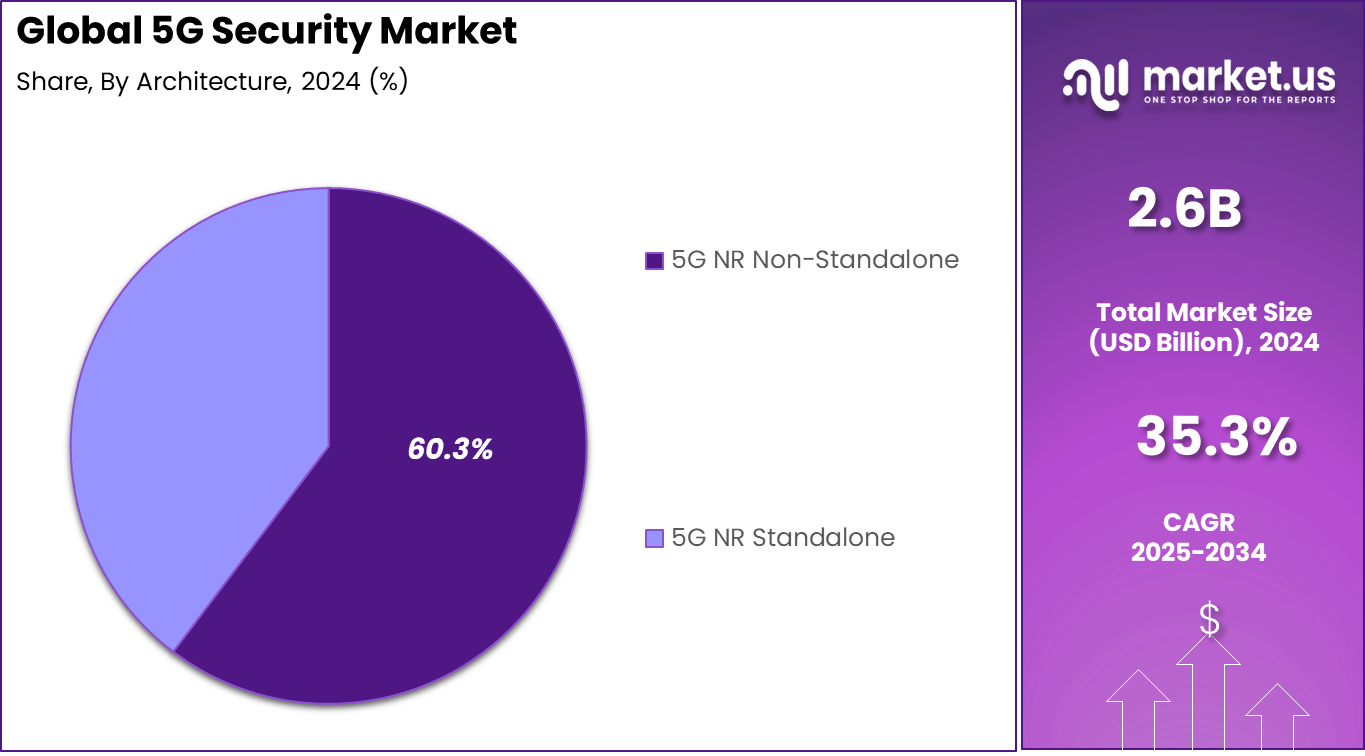
- The 5G NR Non-Standalone (NSA) architecture accounted for 60.3%, supported by ongoing 5G rollout phases that rely on existing LTE infrastructure for coverage expansion.
- Telecom Operators held the largest end-user share at 71.3%, as carriers invest heavily in securing network cores, endpoints, and data transmission layers.
- The Smart Manufacturing application captured 25.6%, highlighting the growing use of 5G-enabled industrial systems requiring ultra-reliable, low-latency network security.
- Asia-Pacific represented 38.4% of the global market, supported by rapid 5G adoption and strong government-led cybersecurity frameworks.
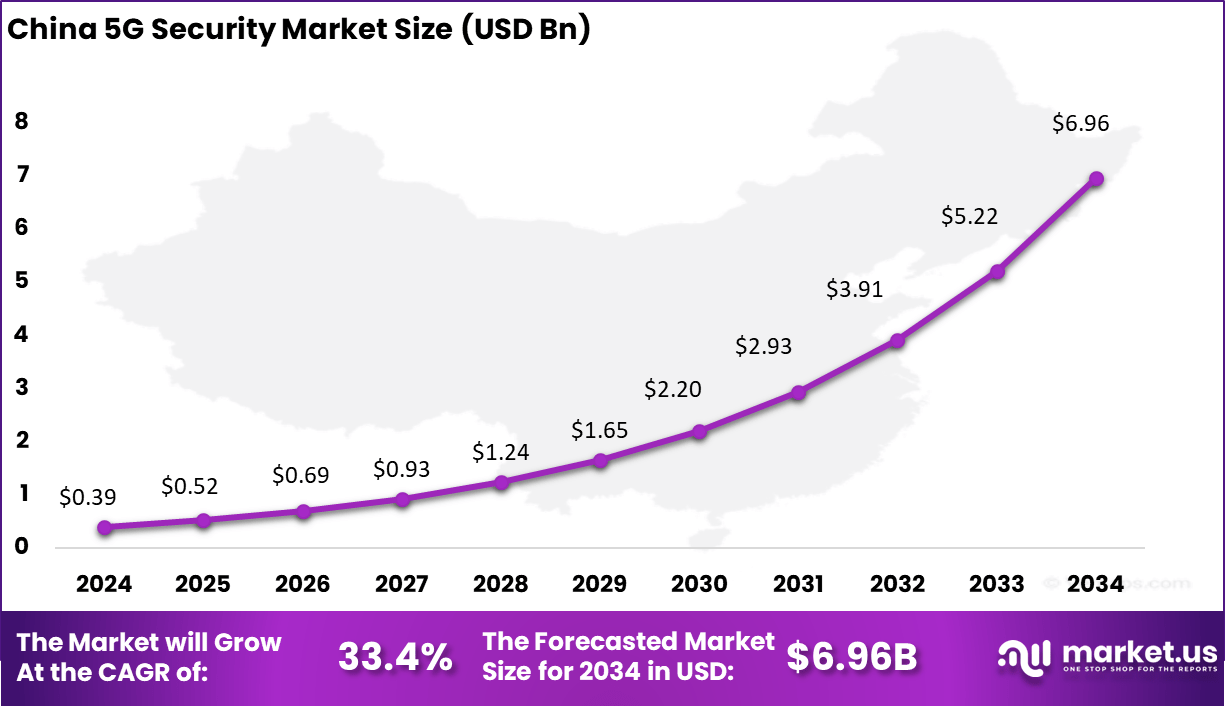
- China reached USD 0.39 Billion in 2024, expanding at a robust 33.4% CAGR, fueled by large-scale 5G deployment and national investments in secure digital infrastructure.
Key 5G Cyberthreat Statistics
- Increased IoT threat level: 70% of executives view the rising number of 5G-connected devices as a major security risk.
- IoT traffic vulnerability: 98% of IoT traffic remains unencrypted, exposing sensitive personal and operational data.
- Attack surface expansion: Billions of interconnected IoT devices dramatically increase the number of potential attack entry points.
- Persistent legacy risks: 85% of mobile operators plan to continue using older 2G/3G networks, introducing legacy security flaws into hybrid 5G environments.
- AI-powered attacks: In 2025, 16% of breaches involved AI tools; 37% were phishing campaigns, and 35% leveraged deepfake attacks.
Role of Generative AI
Generative AI plays a crucial role in transforming 5G security by enhancing threat detection and response capabilities across the entire network architecture. It enables real-time monitoring of devices, data traffic, and network components, effectively identifying unusual patterns and potential breaches. Generative AI simulates cyberattacks and realistic threat scenarios, enabling security teams to test and strengthen network defenses proactively and prevent vulnerabilities before exploitation.
A significant 5G market report confirms that AI integration in security solutions is becoming essential, with about 43% of threat detection systems now relying on AI-driven analysis. Moreover, generative AI contributes to developing advanced encryption protocols that adapt dynamically to evolving security needs in 5G networks. This includes securing data transit between core network elements and user devices, making interception and unauthorized access harder.
AI also enhances physical layer security techniques, such as beamforming and artificial noise injection, to deter eavesdropping. According to recent data, the adoption of AI-powered security solutions in 5G networks has grown by over 40% in just the past year, highlighting the growing trust in AI’s ability to safeguard next-generation networks.
Regional Insight: Asia-Pacific and China
Asia-Pacific holds the largest regional share with 38.4%, driven by aggressive 5G deployment programs and strong government-backed security frameworks. Countries like South Korea, Japan, and India are actively conducting trials to integrate native encryption and network slicing protection technologies. Rapid industrial digitalization and smart city initiatives motivate enterprises to include cybersecurity within the core of 5G infrastructure planning.
China accounts for about USD 0.39 billion, growing at an impressive 33.4% CAGR. Its rapid rollout of independent 5G networks and development of indigenous security algorithms contribute significantly to market growth. Chinese firms are leveraging AI and zero-trust principles to counter advanced persistent threats targeting communication and IoT systems. With widespread adoption in both metropolitan and industrial regions, China continues to shape global benchmarks for high-speed, secure 5G connectivity.
Emerging Trends in 5G Security
One rising trend in 5G security is the shift towards zero-trust security models, where continuous verification and strict access controls replace traditional perimeter-based defenses. This approach is supported by AI-powered analytics that monitor user behavior and network activities to detect anomalies instantly.
Another trend is the increased focus on securing network slices, which allows multiple virtual networks to operate on a single physical 5G infrastructure, each with bespoke security policies. Industry data shows that over 35% of network operators are currently implementing zero-trust frameworks combined with AI to mitigate sophisticated cyber threats.
Additionally, securing edge computing environments is becoming a top priority as 5G drives data processing closer to the user. Edge security measures involve AI-based threat detection systems designed specifically to protect real-time data flows and IoT device clusters at the network’s periphery. Recent statistics indicate that investment in edge security solutions has increased by 42%, reflecting the urgent need to protect decentralized assets and sensitive data.
Growth Factors
The rapid expansion of 5G networks and the explosion of connected devices, especially IoT endpoints, are key drivers for the increasing demand for robust 5G security solutions. With billions of new connections, the attack surface widens, necessitating more sophisticated and scalable security measures.
Research shows a 40% year-over-year increase in 5G security deployments, directly correlated with network expansion and the rising awareness of cyber risks linked to 5G-enabled applications like autonomous vehicles and industrial automation. Another growth factor is the urgent need to secure ultra-reliable low-latency communications (URLLC), which support critical use cases requiring near-instantaneous data transfer.
Security failures in such contexts can have severe consequences on safety and data integrity, pushing organizations to adopt advanced encryption, threat detection, and network segmentation techniques. Data reveals that 45% of 5G security investments are now focused on protecting URLLC and critical infrastructure segments, underscoring the high stakes involved.
By Offering
In 2024, Solutions dominate the 5G security market with 65.4% share. Organizations are increasingly choosing comprehensive software-based tools that secure network operations, user data, and cloud communication layers. These solutions address identity verification, encryption, threat detection, and traffic monitoring.
As 5G networks expand, telecom and enterprise operators are prioritizing scalable, AI-driven security models that adapt to fast-changing network topologies. This strong uptake highlights growing trust in integrated defenses over fragmented hardware approaches.
The prominence of solutions is also supported by the need for automation and analytics in managing complex 5G infrastructures. Real-time insights help operators mitigate potential intrusions as devices and applications proliferate across networks. Vendors are embedding policy enforcement, intrusion prevention, and visibility features to detect anomalies early.
By Network Component Security
In 2024, Radio Access Network (RAN) security leads with a 55.7% share. The RAN layer remains highly vulnerable because of increased virtualization and the use of open interfaces in 5G systems. Protection strategies now focus on securing baseband signals, authenticating network nodes, and encrypting backhaul data.
Stronger RAN defense frameworks are essential as more small cells and edge nodes become operational, increasing entry points for cyber-attacks. Investments in RAN shielding also align with government cybersecurity mandates targeting 5G infrastructure resilience. Enhanced encryption methods and authentication protocols are being implemented to prevent interference or unauthorized signal interception.
With multiple vendors participating in open RAN models, interoperability testing has become central to ensuring consistent protection across hardware and software domains. The combination of policy-based management and continuous monitoring reinforces this segment’s leading position in 5G network defense.
By Architecture
In 2024, The 5G NR Non-Standalone (NSA) architecture holds around 60.3% of the market. Most early 5G networks rely on existing 4G LTE cores, making it crucial to integrate hybrid security structures. This model offers a practical upgrade path while demanding additional safeguards across interlinked radio and core domains.
Operators continue to strengthen identity management, session encryption, and inter-network trust systems to prevent vulnerabilities arising from mixed-generation infrastructure. NSA deployments also benefit from maturity in existing LTE protection standards, reducing the learning curve for telecom security teams. However, this architecture still requires dynamic frameworks to handle 5G data traffic complexities.
Efforts are focused on minimizing downtimes from cyber disruptions and enabling reliable coordination between cloud and edge security layers. The adaptability of NSA systems explains their ongoing preference among operators moving gradually toward full 5G adoption.
By End User
In 2024, Telecom operators account for about 71.3% of end-user demand in the 5G security space. As they expand national and private 5G networks, these operators face increased responsibility for data integrity, user authentication, and infrastructure resilience.
Security has become integral to network orchestration, influencing design, deployment, and customer trust. The heavy reliance on distributed cloud architecture has made continuous 5G protection indispensable to core operations. Operators are raising investment in threat analytics platforms capable of identifying attacks across vast device ecosystems.
The need for 24/7 monitoring across thousands of nodes demands automation, artificial intelligence, and advanced encryption capabilities. As more critical operations – such as smart manufacturing and e-health – connect through carrier networks, telecom entities are expected to set global benchmarks for standardized 5G protection frameworks.
By Application
In 2024, Smart manufacturing represents 25.6% of the 5G security market’s application share. Industrial automation and connected equipment rely heavily on secure, high-speed wireless links to operate safely and efficiently. As factories adopt autonomous robots, digital twins, and sensor networks, the necessity to safeguard data integrity and operational continuity intensifies.
Secure network slicing ensures that production lines and machines communicate without external interference. The growing presence of industrial IoT devices increases the number of attack surfaces, prompting manufacturers to adopt real-time anomaly detection and encrypted machine communication.
Cyber resilience has become a foundation for Industry 4.0 objectives, enabling safe adoption of remote control and smart maintenance systems. Security strategies now emphasize end-to-end visibility to maintain both productivity and compliance with safety standards.
Key Market Segments
By Offering
- Solutions
- Next-Generation Firewall
- Data Loss Prevention
- Antivirus/Antimalware
- Distributed Denial of Service Protection
- Security Gateway
- Sandboxing
- Others
- Services
- Consulting
- Implementation
- Support & Maintenance
By Network Component Security
- Radio Access Network Security
- Mobile Core Security
By Architecture
- 5G NR Standalone
- 5G NR Non-Standalone
By End-User
- Telecom Operators
- Enterprises
By Application
- Virtual & Augmented Reality
- Connected Automotive
- Smart Manufacturing
- Wireless EHealth
- Smart Cities
- Others
By Vertical
- Manufacturing
- Healthcare
- Energy & Utilities
- Retail
- Automotive & Transportation
- Public Safety
- Media & Entertainment
- Others
Key Regions and Countries
- North America
- US
- Canada
- Europe
- Germany
- France
- The UK
- Spain
- Italy
- Russia
- Netherlands
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- India
- Australia
- Singapore
- Thailand
- Vietnam
- Rest of APAC
- Latin America
- Brazil
- Mexico
- Rest of Latin America
- Middle East & Africa
- South Africa
- Saudi Arabia
- UAE
- Rest of MEA
Drivers
Growing Need for Advanced Network Security
The expanding deployment of 5G networks is a key driver for increasing security measures. As 5G offers faster speeds and supports a vast number of connected devices, the risk of cyber threats has grown significantly. The technology’s ability to enable critical applications like smart cities and autonomous vehicles demands robust security frameworks to protect sensitive data and infrastructure.
Governments and businesses are investing more to secure their networks, and spending on 5G security is projected to surge in response to these evolving threats. This increasing investment underscores the importance placed on safeguarding the immense data flow and operational continuity of 5G services.
Restraints
High Deployment and Maintenance Costs
One major restraint limiting the rapid adoption of comprehensive 5G security is the high cost involved. Implementing advanced security solutions requires substantial capital investment in new hardware, software, and skilled personnel. Many telecom providers, especially in emerging markets, find these expenses a barrier to deploying full-scale security protocols.
Additionally, maintaining and updating security measures in the complex 5G infrastructure adds ongoing costs and operational challenges. These financial and resource barriers slow down the widespread adoption of the most robust security solutions. As a result, some networks remain vulnerable, risking future security breaches.
Opportunities
AI and Machine Learning Integration
The integration of artificial intelligence (AI) and machine learning (ML) presents a huge opportunity in 5G security. These advanced technologies can analyze large volumes of network data in real time to identify unusual activity and potential threats quickly. AI-driven threat detection can help in preempting cyberattacks before they cause damage, making networks more resilient.
As 5G networks expand, AI and ML will play an essential role in creating adaptive security systems that evolve with emerging threats. This opportunity is expected to be a game-changer, enabling proactive rather than reactive security postures in 5G infrastructure.
Challenges
Security Standardization and Fragmentation
One of the toughest challenges for 5G security is establishing universal standards across different regions and vendors. The rapid evolution of 5G technology, coupled with diverse regulations and varying levels of infrastructure maturity, leads to fragmentation. Different operators may adopt varying security protocols, creating gaps and inconsistencies that cybercriminals can exploit.
The lack of standardized, comprehensive security frameworks hampers efforts to implement end-to-end security. Addressing this challenge requires international cooperation and the development of universally accepted cybersecurity standards to ensure all parts of the 5G ecosystem are equally protected.
Key Players Analysis
The 5G Security Market is underpinned by major network equipment manufacturers such as Ericsson, Huawei, Nokia, and ZTE. These companies develop core 5G network infrastructure, including the 5G core, RAN (radio access network), and network slicing features, and integrate advanced security mechanisms to protect network integrity, data confidentiality, and service availability. Their solutions are critical for telecom operators rolling out 5G services globally.
Cybersecurity vendors including Palo Alto Networks, Check Point Software Technologies Ltd., Fortinet, Inc., A10 Networks, Inc., and Trend Micro deliver specialized 5G security appliances and software such as virtualized firewalls, edge encryption, and threat detection for mobile networks. These providers enable telcos to secure mobile edge computing (MEC), IoT endpoints, and network slices against evolving threats. Their offerings strengthen the security posture of enterprise and consumer 5G services.
Telecom operators and test-service specialists such as AT&T, F5, Inc., Spirent Communications, Allot, and Mobileum, along with Cisco, Thales, Juniper Networks, and other market participants, contribute to security through anomaly detection, network monitoring, fraud prevention, and regulatory compliance. Their integration of 5G-specific security frameworks ensures that network operators can deliver reliable, secure connectivity in sectors such as autonomous vehicles, smart cities, and industrial IoT deployments.
Top Key Players in the Market
- ERICSSON
- Palo Alto Networks
- Thales
- A10 Networks, Inc.
- Allot
- AT&T
- F5, Inc.
- Check Point Software Technologies Ltd.
- Fortinet, Inc.
- Spirent Communications
- Cisco
- Huawei
- Nokia
- Juniper Networks
- Mobileum
- ZTE
- Trend Micro
- Others
Recent Developments
- March 2025, Palo Alto Networks launched Prisma SASE 5G, a cloud-native Zero Trust security offering designed to secure enterprise 5G networks. It integrates SIM-based authentication, AI-driven threat detection, and partners with Nokia, NVIDIA, NTT DATA, and Telenor to enhance private 5G security globally. This launch strengthens enterprise 5G protection amid rising cyber threats.
- February 2025, NTT DATA partnered with Palo Alto Networks to offer a managed security service for private 5G industrial deployments. This service combines Palo Alto’s next-gen firewall capabilities with NTT DATA’s private 5G architecture, focusing on network visibility, access control, and automated threat detection tailored for operational technology environments.
- July 2025, F5 acquired MantisNet, enhancing its flagship Application Delivery and Security Platform with real-time network observability and intelligence specifically for cloud-native and 5G environments. This acquisition allows deeper insight and faster responses to network-level security threats in virtualized 5G infrastructures.
Report Scope
Report Features Description Market Value (2024) USD 2.6 Bn Forecast Revenue (2034) USD 53.9 Bn CAGR(2025-2034) 35.3% Base Year for Estimation 2024 Historic Period 2020-2023 Forecast Period 2025-2034 Report Coverage Revenue forecast, AI impact on Market trends, Share Insights, Company ranking, competitive landscape, Recent Developments, Market Dynamics, and Emerging Trends Segments Covered By Offering (Solutions (Next-Generation Firewall, Data Loss Prevention, Antivirus/Antimalware, Distributed Denial of Service Protection, Security Gateway, Sandboxing, Others), Services (Consulting, Implementation, Support & Maintenance), By Network Component Security (Radio Access Network Security, Mobile Core Security), By Architecture (5G NR Standalone, 5G NR Non-Standalone), By End-User (Telecom Operators, Enterprises), By Application (Virtual & Augmented Reality, Connected Automotive, Smart Manufacturing, Wireless EHealth, Smart Cities, Others), By Vertical (Manufacturing, Healthcare, Energy & Utilities, Retail, Automotive & Transportation, Public Safety, Media & Entertainment, Others.) Regional Analysis North America – US, Canada; Europe – Germany, France, The UK, Spain, Italy, Russia, Netherlands, Rest of Europe; Asia Pacific – China, Japan, South Korea, India, New Zealand, Singapore, Thailand, Vietnam, Rest of Latin America; Latin America – Brazil, Mexico, Rest of Latin America; Middle East & Africa – South Africa, Saudi Arabia, UAE, Rest of MEA Competitive Landscape ERICSSON, Palo Alto Networks, Thales, A10 Networks, Inc., Allot, AT&T, F5, Inc., Check Point Software Technologies Ltd., Fortinet, Inc., Spirent Communications, Cisco, Huawei, Nokia, Juniper Networks, Mobileum, ZTE, Trend Micro, Others. Customization Scope Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements. Purchase Options We have three licenses to choose from: Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited Users, Printable PDF) Frequently Asked Questions (FAQ)
What is the 5G Security Market?The 5G security market encompasses solutions and services that aim to protect networks, applications, and connected devices that utilize 5G technology, ensuring that they are safeguarded against cyber threats and attacks.
How big is 5G Security Market?The Global 5G Security Market size is expected to be worth around USD 39.5 Billion By 2033, from USD 1.6 Billion in 2023, growing at a CAGR of 37.8% during the forecast period from 2024 to 2033.
What are the major drivers in the 5G Security Market?Key drivers include heightened security concerns around 5G networks, an increase in IoT connections requiring robust security measures, rising ransomware attacks on IoT devices, and increasing attacks on critical infrastructure.
Who are the key players in the 5G Security Market?Notable companies in the market include A10 Networks, Akamai Allot, AT&T, Avast, Check Point, Cisco Systems, Ericsson, F5 Networks, ForgeRock, Fortinet, G+D Mobile Security, Huawei, Juniper Networks, Nokia, Palo Alto Networks, Other Key Players
What are the key trends and segments in the 5G Security Market?The market is segmented based on deployment types like cloud and on-premise, with cloud deployments preferred due to their scalability, flexibility, and efficiency. Key application areas include virtual and augmented reality, autonomous systems, smart cities, and connected automotive sectors.
What challenges does the 5G Security Market face?One of the major challenges in the 5G security market is the complexity of securing an expanding network of devices and endpoints. As 5G enables higher connectivity across a range of devices, it increases the potential attack surface for cyber threats. Ensuring comprehensive security that can scale with these networks is a significant challenge.

-
-
- ERICSSON
- Palo Alto Networks
- Thales
- A10 Networks, Inc.
- Allot
- AT&T
- F5, Inc.
- Check Point Software Technologies Ltd.
- Fortinet, Inc.
- Spirent Communications
- Cisco
- Huawei
- Nokia
- Juniper Networks
- Mobileum
- ZTE
- Trend Micro
- Others













