Global Zero Trust Security Models in ERP Market Size, Share Analysis Report By Authentication (Single-factor, Multi-factor), By Type (Network Security, Data Security, Endpoint Security, On-premises Security, Others), By Enterprise Size (SMEs, Large Enterprises), By End Use (BFSI, Healthcare, Retail, IT & Telecom, Others), Region and Companies - Industry Segment Outlook, Market Assessment, Competition Scenario, Trends and Forecast 2024-2033
- Published date: May 2025
- Report ID: 147505
- Number of Pages: 356
- Format:
-
keyboard_arrow_up
Quick Navigation
Report Overview
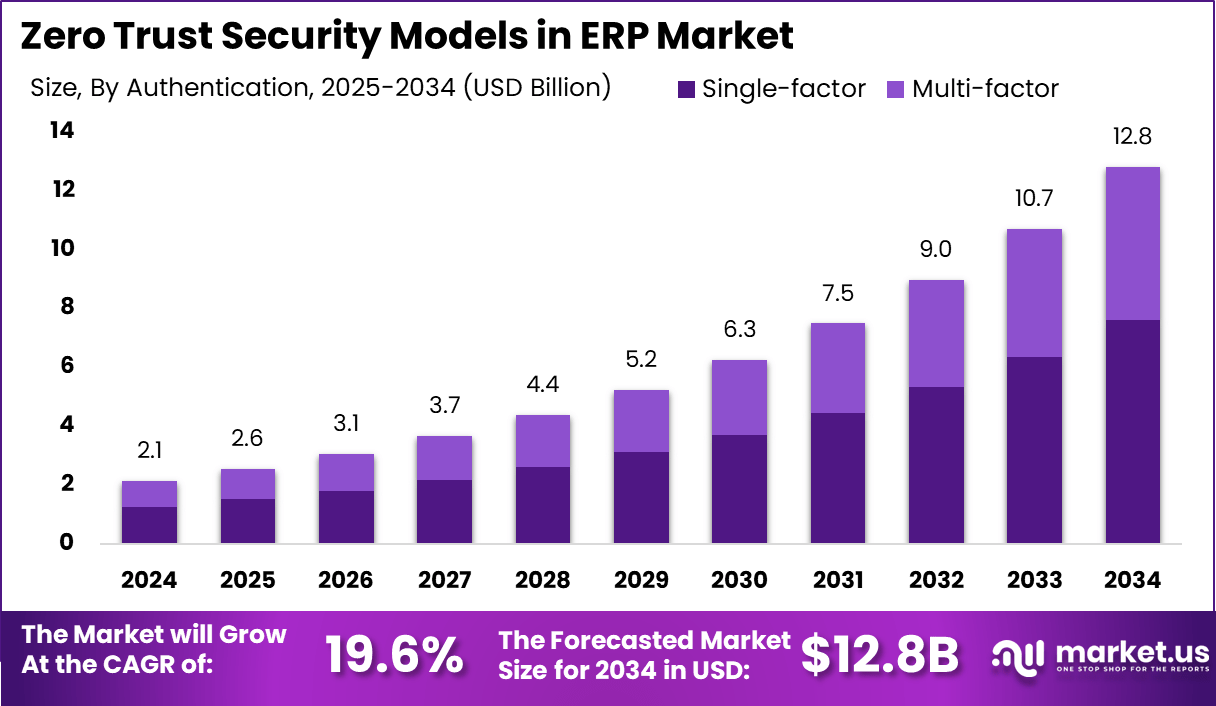
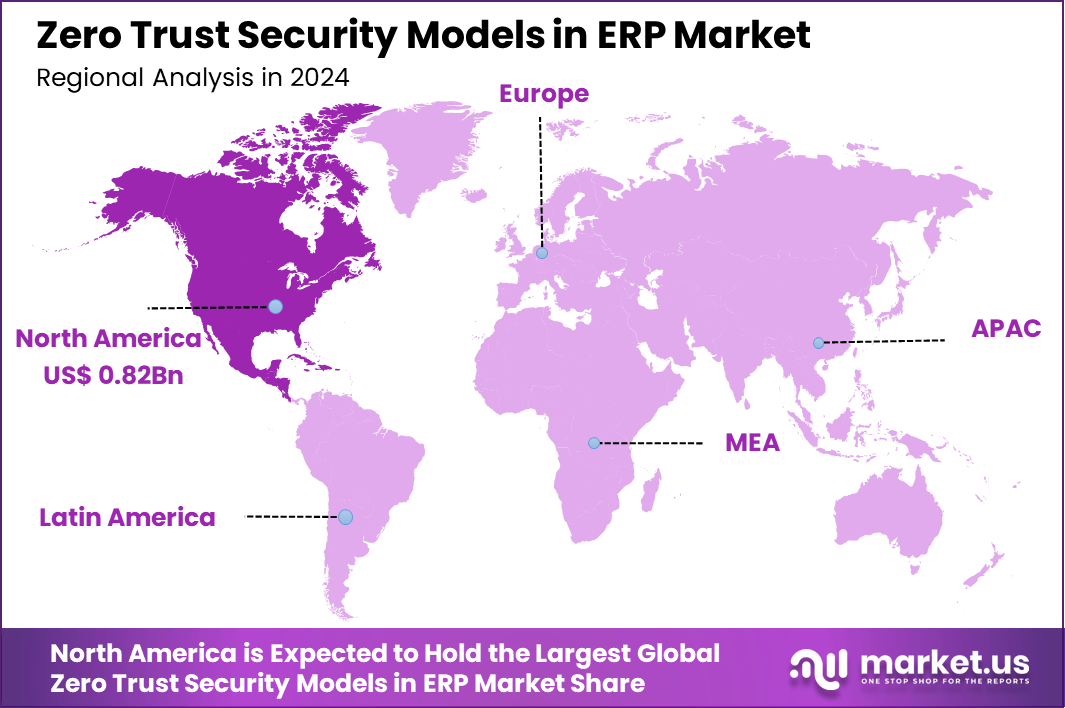
The Global Zero Trust Security Models in ERP Market size is expected to be worth around USD 12.8 Billion By 2034, from USD 2.1 billion in 2024, growing at a CAGR of 19.6% during the forecast period from 2025 to 2034. In 2024, North America held a dominant market position, capturing more than a 39.4% share, holding USD 0.8 Billion revenue.
The Zero Trust Security Model in Enterprise Resource Planning (ERP) systems represents a paradigm shift in cybersecurity. This model operates on the principle of “never trust, always verify,” ensuring that every user and device, regardless of their location within or outside the network perimeter, undergoes strict identity verification before accessing ERP resources. By treating all network traffic as potentially hostile, Zero Trust Security minimizes the risk of unauthorized access and data breaches within ERP environments.
Key factors propelling this growth include the need for stringent regulatory compliance, the rise in sophisticated cyber-attacks, and the expanding use of Bring Your Own Device (BYOD) policies. Organizations are increasingly investing in Zero Trust solutions, such as multi-factor authentication (MFA), micro-segmentation, identity and access management (IAM), and endpoint security, to safeguard their ERP systems.
The demand for Zero Trust Security in ERP is further amplified by the growing awareness of data privacy concerns and the necessity for robust security frameworks to protect sensitive business information. As enterprises continue to digitize their operations, the implementation of Zero Trust principles becomes imperative to ensure the integrity and confidentiality of ERP data.
As per the latest insights from market.us, The global Zero Trust Security market is witnessing a significant transformation, driven by the growing demand for identity-centric security frameworks across digital enterprises. In 2023, the market was valued at USD 30.3 Billion, and it is projected to reach a substantial USD 144.4 Billion by 2033, reflecting a strong compound annual growth rate (CAGR) of 16.9% during the forecast period from 2024 to 2033.
Technological advancements, including the integration of artificial intelligence (AI) and machine learning (ML) in security protocols, are enhancing the capabilities of Zero Trust models. These technologies enable real-time threat detection and response, thereby strengthening the security posture of ERP systems.
The regulatory environment also plays a crucial role in the adoption of Zero Trust Security. Compliance with standards such as the General Data Protection Regulation (GDPR) and the National Institute of Standards and Technology (NIST) guidelines necessitates the implementation of comprehensive security measures, including Zero Trust architectures.
Key Takeaways
- The global Zero Trust Security Models in ERP market is projected to grow from USD 2.1 billion in 2024 to USD 12.8 billion by 2034, reflecting a powerful CAGR of 19.6%, as businesses increasingly prioritize identity-based access and continuous authentication in ERP systems.
- In 2024, North America led with 39.4% of the global market share, generating USD 0.8 billion in revenue, driven by strong regulatory frameworks and early adoption of zero trust architecture in mission-critical enterprise software.
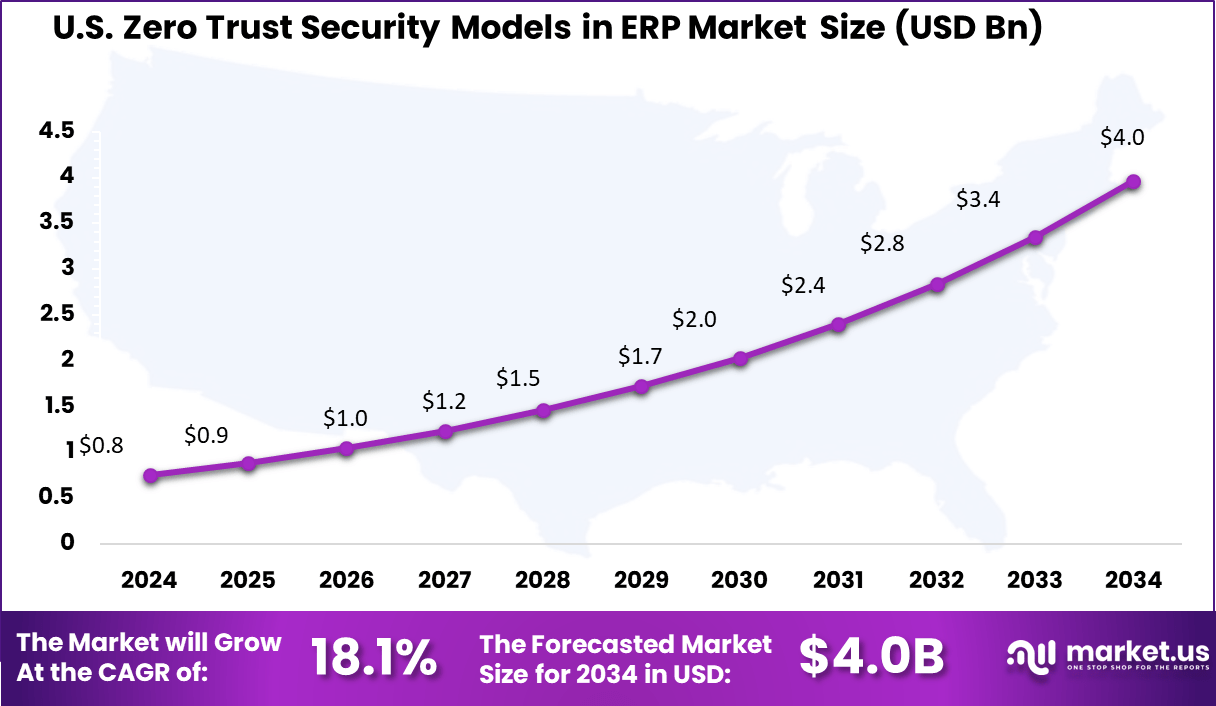
- The US market alone stood at USD 0.8 billion in 2024, and is forecast to reach USD 4.0 billion by 2034, expanding at a healthy CAGR of 18.1%, supported by large-scale digital transformation in ERP infrastructures across federal and Fortune 500 firms.
- Among authentication types, Single-Factor Authentication (SFA) dominated in 2024 with 59.4% share, due to its cost-effectiveness and wide use in legacy ERP systems, though it’s expected to give way to multi-factor and biometric solutions in coming years.
- The Network Security segment led the technology landscape, capturing 26.8% of global market share in 2024, as companies focused on internal segmentation and real-time traffic validation to protect ERP workflows.
- Large Enterprises contributed over 71.4% of market revenue in 2024, highlighting their need for robust, scalable zero trust solutions to secure complex ERP environments across distributed teams and third-party integrations.
- The BFSI sector emerged as the top end-user segment, holding 25.3% of the global share in 2024, driven by intense compliance requirements and the criticality of ERP-linked financial data.
US Market Growth
The US Zero Trust Security Models in ERP Market is valued at approximately USD 0.8 Billion in 2024 and is predicted to increase from USD 0.9 Billion in 2025 to approximately USD 4.0 Billion by 2034, projected at a CAGR of 18.1% from 2025 to 2034.
In 2024, North America held a dominant market position in the Zero Trust Security Models in ERP market, capturing more than a 39.4% share and generating approximately USD 0.8 billion in revenue. This regional dominance can be primarily attributed to the mature digital infrastructure across the United States and Canada, coupled with the high incidence of targeted cyber threats.
Organizations across sectors such as finance, manufacturing, and healthcare have been proactive in deploying Zero Trust frameworks within their ERP systems to minimize data breach risks and comply with evolving cybersecurity mandates. The region has seen rapid adoption of multi-factor authentication, micro-segmentation, and identity-centric security controls as businesses shift to hybrid and remote operational models.
Authentication Analysis
In 2024, the Single-Factor Authentication (SFA) segment held a dominant position in the Zero Trust Security Models in ERP market, capturing over 59.4% of the global share. This prevalence is largely attributed to the widespread use of traditional password-based systems, which are deeply integrated into many organizations’ existing ERP infrastructures.
The familiarity and ease of implementation of SFA make it a preferred choice for businesses seeking straightforward access control mechanisms without the complexity of additional verification steps. However, the cybersecurity landscape is evolving rapidly, and the limitations of SFA are becoming increasingly apparent.
As a result, there is a growing shift towards Multi-Factor Authentication (MFA) solutions, which combine multiple verification methods to enhance security. MFA’s ability to provide a more robust defense against unauthorized access is leading to its increased adoption, particularly in sectors where data sensitivity and regulatory compliance are paramount.
Type Analysis Analysis
In 2024, the Network Security segment held a dominant position in the Zero Trust Security Models in ERP market, capturing over 26.8% of the global share. This prominence is largely due to the increasing need for secure network infrastructures as organizations transition to cloud-based ERP systems and adopt remote work models.
The shift has expanded the attack surface, making robust network security measures essential to protect sensitive enterprise data from cyber threats. The adoption of Zero Trust principles in network security involves continuous verification of user identities and strict access controls, ensuring that only authorized personnel can access specific network resources.
This approach minimizes the risk of unauthorized access and lateral movement within the network, which is crucial for safeguarding ERP systems that handle critical business operations. Furthermore, the integration of advanced technologies such as AI and machine learning enhances the ability to detect and respond to anomalies in real-time, strengthening the overall security posture.
The dominance of the Network Security segment is also supported by regulatory requirements and compliance standards that mandate stringent security protocols for data protection. Organizations are compelled to implement comprehensive network security frameworks to meet these obligations, thereby driving the demand for Zero Trust solutions in this segment.
Enterprise Size Analysis
In 2024, the Large Enterprises segment held a dominant position in the Zero Trust Security Models in ERP market, capturing more than a 71.4% share. This leadership is primarily due to the extensive digital infrastructures of large organizations, which encompass complex ERP systems, diverse cloud environments, and a globally distributed workforce.
The necessity to protect vast amounts of sensitive data across multiple locations and devices compels these enterprises to adopt comprehensive Zero Trust frameworks. Such frameworks ensure continuous verification of user identities and strict access controls, minimizing the risk of unauthorized access and data breaches.
Moreover, large enterprises often operate under stringent regulatory requirements, such as GDPR, HIPAA, and SOX, which mandate robust security measures to protect sensitive information. The implementation of Zero Trust Security Models in ERP systems aids in achieving compliance by enforcing policies like least-privilege access and continuous monitoring.
Additionally, the financial and technical resources available to large enterprises facilitate the integration of advanced security solutions, including AI-driven threat detection and real-time analytics, further strengthening their security posture.
End Use Analysis
In 2024, the Banking, Financial Services, and Insurance (BFSI) segment held a dominant position in the Zero Trust Security Models in ERP market, capturing more than a 25.3% share. This leadership is primarily driven by the sector’s critical need to protect sensitive financial data and ensure compliance with stringent regulatory standards.
Financial institutions are increasingly adopting Zero Trust architectures to mitigate risks associated with cyber threats, insider attacks, and data breaches. The implementation of multi-factor authentication, continuous monitoring, and strict access controls within ERP systems has become essential to safeguard customer information and maintain trust.
The BFSI sector’s emphasis on digital transformation and the integration of advanced technologies has further propelled the adoption of Zero Trust Security Models. As financial services increasingly move towards cloud-based solutions and remote operations, the need for robust security frameworks that can adapt to dynamic environments has become paramount.
Zero Trust principles, which operate on the “never trust, always verify” approach, align well with the sector’s requirements for real-time threat detection and response. By implementing these models, financial institutions can enhance their security posture, reduce potential vulnerabilities, and ensure the integrity of their ERP systems.
Key Market Segments
By Authentication
- Single-factor
- Multi-factor
By Type
- Network Security
- Data Security
- Endpoint Security
- On-premises Security
- Others
By Enterprise Size
- SMEs
- Large Enterprises
By End Use
- BFSI
- Healthcare
- Retail
- IT & Telecom
- Others
Key Regions and Countries
North America
- US
- Canada
Europe
- Germany
- France
- The UK
- Spain
- Italy
- Russia
- Netherlands
- Rest of Europe
Asia Pacific
- China
- Japan
- South Korea
- India
- Australia
- Singapore
- Thailand
- Vietnam
- Rest of APAC
Latin America
- Brazil
- Mexico
- Rest of Latin America
Middle East & Africa
- South Africa
- Saudi Arabia
- UAE
- Rest of MEA
Driver
Rising Cybersecurity Threats and Regulatory Pressures
The increasing frequency and sophistication of cyberattacks have necessitated a shift towards more robust security frameworks. Zero Trust Security Models have emerged as a critical response to these evolving threats, particularly within Enterprise Resource Planning (ERP) systems.
Traditional security models, which often rely on perimeter defenses, are no longer sufficient in the face of advanced persistent threats and insider risks. Zero Trust operates on the principle of “never trust, always verify,” ensuring that every access request is thoroughly authenticated and authorized, regardless of its origin.
Regulatory compliance further drives the adoption of Zero Trust in ERP systems. Legislations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) mandate stringent data protection measures. Implementing Zero Trust frameworks aids organizations in meeting these regulatory requirements by providing granular access controls and continuous monitoring capabilities.
Restraint
Integration Challenges with Legacy ERP Systems
The integration of Zero Trust Security Models into existing ERP systems presents significant challenges, primarily due to the complexity and rigidity of legacy infrastructures. Many organizations operate ERP systems that were not designed with modern security paradigms in mind, making the implementation of Zero Trust principles a complex endeavor.
Legacy ERP systems often lack the necessary interfaces and capabilities to support continuous authentication and real-time access controls inherent in Zero Trust architectures. This incompatibility necessitates extensive system overhauls or the deployment of additional security layers, leading to increased costs and extended implementation timelines.
Opportunity
Enhancing Operational Resilience through Zero Trust
The adoption of Zero Trust Security Models within ERP systems offers a strategic opportunity to enhance operational resilience and data integrity. By implementing strict access controls and continuous verification processes, organizations can significantly reduce the risk of unauthorized access and data breaches.
Zero Trust frameworks enable the segmentation of ERP environments, allowing for more precise control over user access to sensitive data and critical business functions. This segmentation not only mitigates the potential impact of security incidents but also facilitates compliance with data protection regulations by ensuring that access to personal and sensitive information is tightly controlled and monitored.
Challenge
Balancing Security and User Experience
Implementing Zero Trust Security Models in ERP systems necessitates a delicate balance between stringent security measures and maintaining a seamless user experience. The continuous authentication and authorization processes central to Zero Trust can introduce friction into user workflows, potentially impacting productivity and user satisfaction.
Users accustomed to traditional access models may find the additional security steps cumbersome, leading to resistance and potential circumvention of security protocols. This resistance can undermine the effectiveness of the Zero Trust framework, as users seek workarounds that may compromise system security.
To address this challenge, organizations must invest in user education and change management strategies that emphasize the importance of security measures and their role in protecting organizational assets. Additionally, leveraging adaptive authentication technologies can help minimize user friction by tailoring security requirements to the context of each access request, thereby preserving the user experience while maintaining robust security postures.
Growth Factors
The adoption of Zero Trust Security Models in Enterprise Resource Planning (ERP) systems is being driven by several key factors:
- Increasing Cybersecurity Threats: The rise in sophisticated cyberattacks, including ransomware and insider threats, has necessitated a shift from traditional perimeter-based security to a more robust Zero Trust approach.
- Remote Work and BYOD Trends: The proliferation of remote work and Bring Your Own Device (BYOD) policies has expanded the attack surface, making it imperative to implement security models that do not automatically trust any device or user.
- Regulatory Compliance Requirements: Stringent data protection regulations such as GDPR and HIPAA require organizations to have stringent access controls and data protection measures, which are inherent in Zero Trust architectures.
- Cloud Adoption: The migration of ERP systems to cloud environments has underscored the need for security models that can operate effectively in dynamic and distributed infrastructures.
Emerging Trends
Several trends are shaping the implementation of Zero Trust in ERP systems:
- Integration with Identity and Access Management (IAM): Organizations are increasingly integrating Zero Trust principles with IAM solutions to ensure that only authenticated and authorized users can access ERP resources.
- Micro-Segmentation: This involves dividing the network into smaller segments to prevent lateral movement of threats, ensuring that even if one segment is compromised, the threat does not spread.
- Continuous Monitoring and Analytics: Employing real-time monitoring tools to analyze user behavior and detect anomalies, thereby enabling prompt response to potential security incidents.
- Adoption of AI and Machine Learning: Leveraging AI and ML to enhance threat detection capabilities and automate response mechanisms within ERP systems.
Business Benefits
Implementing Zero Trust Security Models in ERP systems offers several advantages:
- Enhanced Security Posture: By verifying every access request, organizations can significantly reduce the risk of unauthorized access and data breaches.
- Improved Compliance: Zero Trust architectures facilitate adherence to regulatory requirements by ensuring strict access controls and comprehensive audit trails.
- Operational Efficiency: Automated authentication processes and reduced reliance on traditional security measures streamline operations and reduce administrative overhead.
- Scalability and Flexibility: Zero Trust models are adaptable to various organizational sizes and structures, allowing for scalable security solutions that evolve with business needs.
- Increased Trust and Reputation: Demonstrating a commitment to robust security measures enhances stakeholder confidence and can serve as a competitive differentiator in the market.
Key Player Analysis
Microsoft has been a dominant force in Zero Trust for ERP, thanks to its deep integration with Azure Active Directory and Microsoft Defender. In May 2024, they rolled out enhanced Zero Trust policies for SAP and Dynamics 365, making it easier for businesses to enforce strict access controls. What sets Microsoft apart is its AI-driven threat detection, which monitors ERP systems in real-time.
Palo Alto made waves in March 2024 with Prisma Cloud for ERP, a new Zero Trust solution designed specifically for Oracle Cloud ERP and Workday. Unlike traditional security tools, Palo Alto’s approach uses AI-based monitoring to detect unusual access patterns and block threats before they cause damage. They’ve also been expanding through strategic partnerships, teaming up with major ERP vendors to embed security directly into their platforms.
Cisco took a big step in January 2025 by launching Cisco Secure Access for ERP, blending Zero Trust Network Access (ZTNA) with multi-factor authentication (MFA). Their solution is perfect for companies with hybrid workforces, ensuring employees can securely access ERP data from anywhere. Cisco has been quiet on acquisitions this year but has instead focused on enhancing its existing products with smarter threat intelligence.
Top Key Players in the Market
- Microsoft Corporation
- Okta, Inc.
- Palo Alto Networks
- Zscaler, Inc.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- Fortinet, Inc.
- Ivanti, Inc.
- Check Point Software Technologies
- Appsian Security
- Others
Recent Developments
- In April 2025, Palo Alto Networks announced its intent to acquire Protect AI, a company specializing in securing AI systems, to help customers discover, manage, and protect against AI-specific security risks.
- In April 2025, Check Point Software Technologies and Illumio announced a strategic partnership to help organizations strengthen security and advance their Zero Trust posture through proactive threat prevention and unified intelligence.
- In May 2024, Microsoft expanded its Zero Trust security solutions for ERP systems like SAP and Dynamics 365, integrating Azure Active Directory and Microsoft Defender for Cloud. This helps businesses enforce strict access controls and real-time threat detection.
Report Scope
Report Features Description Market Value (2023) USD 2.1 Bn Forecast Revenue (2033) USD 12.8 Bn CAGR (2024-2033) 19.6% Base Year for Estimation 2024 Historic Period 2020-2023 Forecast Period 2025-2034 Report Coverage Revenue forecast, AI impact on market trends, Share Insights, Company ranking, competitive landscape, Recent Developments, Market Dynamics and Emerging Trends Segments Covered By Authentication (Single-factor, Multi-factor), By Type (Network Security, Data Security, Endpoint Security, On-premises Security, Others), By Enterprise Size (SMEs, Large Enterprises), By End Use (BFSI, Healthcare, Retail, IT & Telecom, Others) Regional Analysis North America – US, Canada; Europe – Germany, France, The UK, Spain, Italy, Russia, Netherlands, Rest of Europe; Asia Pacific – China, Japan, South Korea, India, New Zealand, Singapore, Thailand, Vietnam, Rest of APAC; Latin America – Brazil, Mexico, Rest of Latin America; Middle East & Africa – South Africa, Saudi Arabia, UAE, Rest of MEA Competitive Landscape Microsoft Corporation, Okta, Inc., Palo Alto Networks, Zscaler, Inc., Cisco Systems, Inc., Cloudflare, Inc., Fortinet, Inc., Ivanti, Inc., Check Point Software Technologies, Appsian Security, Others Customization Scope Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements. Purchase Options We have three license to opt for: Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited User and Printable PDF)  Zero Trust Security Models in ERP MarketPublished date: May 2025add_shopping_cartBuy Now get_appDownload Sample
Zero Trust Security Models in ERP MarketPublished date: May 2025add_shopping_cartBuy Now get_appDownload Sample -
-
- Microsoft Corporation
- Okta, Inc.
- Palo Alto Networks
- Zscaler, Inc.
- Cisco Systems, Inc.
- Cloudflare, Inc.
- Fortinet, Inc.
- Ivanti, Inc.
- Check Point Software Technologies
- Appsian Security
- Others












