Global Container Security Market Size, Share, Statistics Analysis Report By Component (Solution, Services), By Deployment (Cloud, On-premise), By Organization Size (Large enterprises, Small and medium-sized enterprises), By Industry Vertical (BFSI, IT and Telecom, Retail, Healthcare, Manufacturing, Government, Others), Region and Companies - Industry Segment Outlook, Market Assessment, Competition Scenario, Trends and Forecast 2024-2033
- Published date: Nov 2024
- Report ID: 134020
- Number of Pages: 331
- Format:
-
keyboard_arrow_up
Quick Navigation
Report Overview
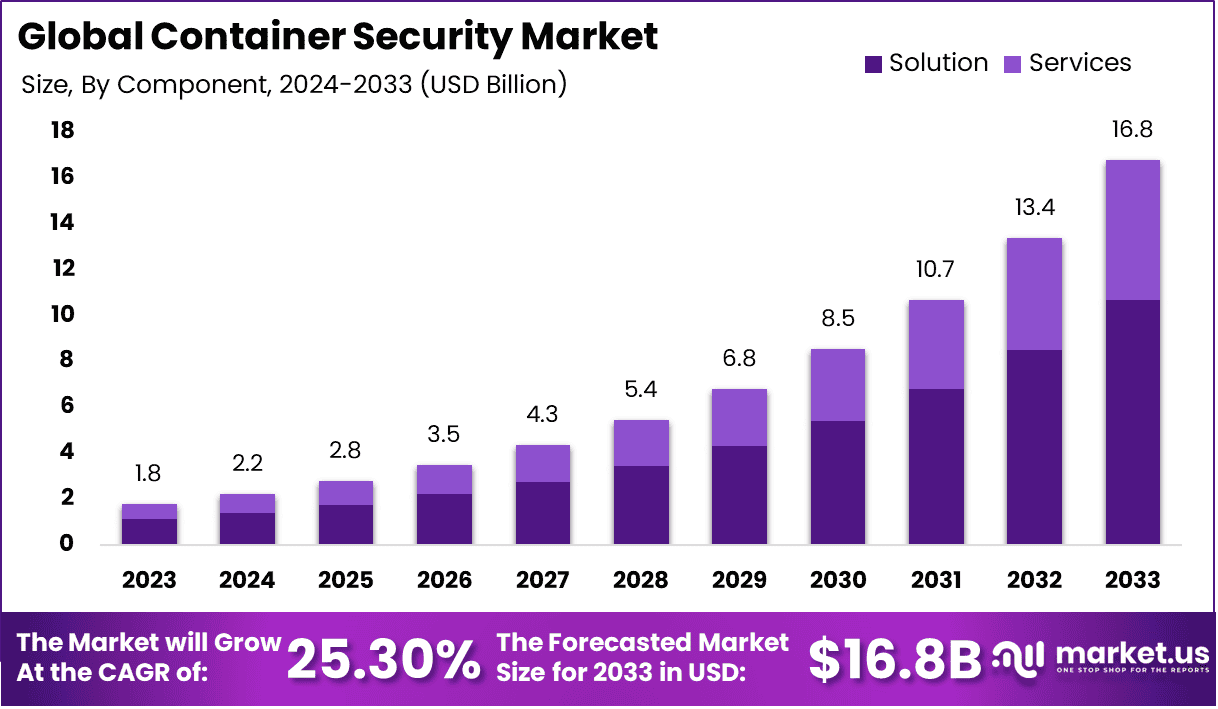
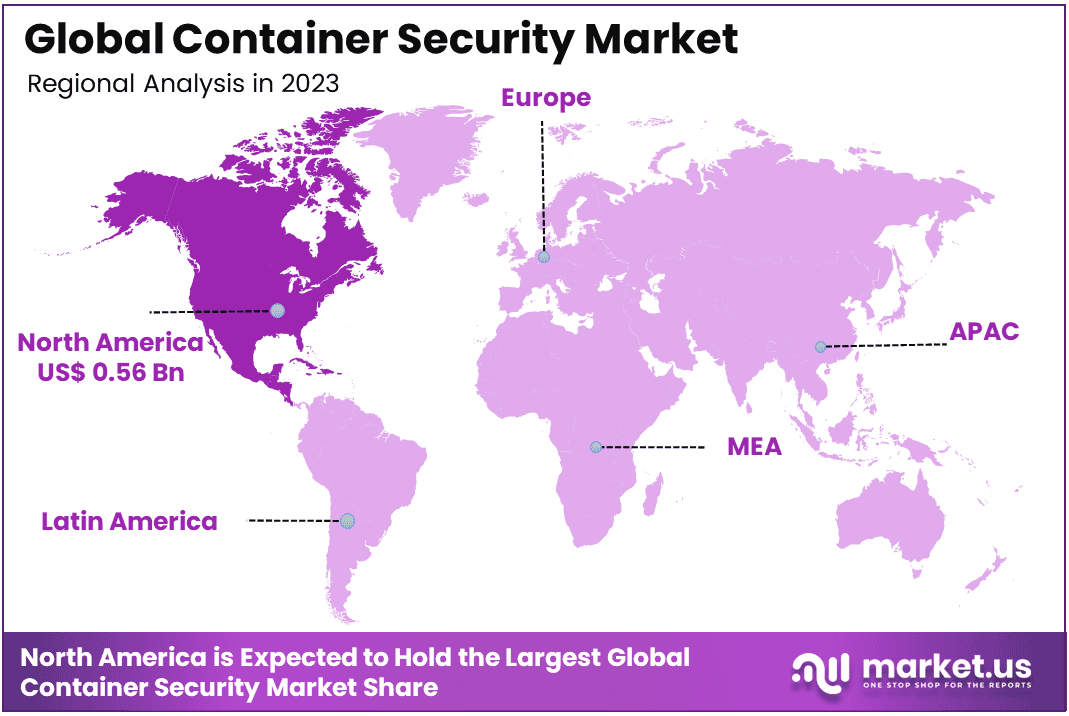
The Global Container Security Market size is expected to be worth around USD 16.8 Billion By 2033, from USD 1.76 Billion in 2023, growing at a CAGR of 25.30% during the forecast period from 2024 to 2033. In 2023, North America held a dominant market position, capturing more than a 32% share, holding USD 1.04 Billion in revenue.
Container security refers to the set of practices and technologies designed to ensure the security and integrity of containerized applications and their underlying infrastructure. Containers, such as Docker or Kubernetes, are increasingly used to deploy applications in a lightweight, portable, and scalable manner. However, as organizations shift to containerized environments, ensuring the security of the entire container lifecycle becomes a critical concern. Container security focuses on safeguarding the container images, container runtime environments, and the orchestration systems that manage containers.
This security practice involves securing the container registry (where images are stored), scanning for vulnerabilities in container images, implementing access controls to prevent unauthorized access, and continuously monitoring containers to detect any abnormal behavior or potential threats. Since containers often run on a shared host operating system, they can become a vector for security breaches if not adequately protected. Container security also involves ensuring compliance with industry regulations and maintaining the confidentiality, integrity, and availability of the data running inside the containers.
With organizations deploying containers at scale for their cloud-native applications, the demand for effective container security tools is accelerating. Container security solutions range from image scanning and vulnerability management to runtime protection and compliance monitoring, all aimed at minimizing risks during container deployment, orchestration, and scaling processes. The market includes security solutions provided by both legacy IT security vendors and newer cybersecurity startups focused specifically on the challenges of containerized environments.
The demand for container security solutions is being driven by the growing number of containerized applications across industries. Large enterprises, as well as small to medium-sized businesses (SMBs), are increasingly moving their workloads to containers to improve operational efficiency, reduce costs, and gain scalability. This surge in container adoption has created a pressing need for container security solutions that can seamlessly integrate into container orchestration platforms like Kubernetes, which is widely used for automating the deployment, scaling, and management of containerized applications.
There are several opportunities in the container security market, primarily driven by the rapid pace of cloud adoption, the move towards DevOps, and the growing shift towards microservices architectures. As organizations migrate legacy applications to the cloud, they increasingly leverage containers for their agility, scalability, and cost-effectiveness. This shift creates a prime opportunity for vendors offering solutions that can provide visibility and protection across containerized environments.
Another significant advancement is the use of runtime protection mechanisms that monitor container behavior during operation, identifying suspicious activity and mitigating threats in real time. This level of proactive defense helps organizations ensure that containerized applications are continuously secure while running at scale. Furthermore, advancements in identity and access management (IAM) for containers are addressing the challenges of managing users and permissions across multiple containerized environments, ensuring that only authorized individuals can access sensitive systems or data.
Container security has become increasingly critical as the adoption of containers accelerates. According to recent statistics, over 60% of organizations have deployed containers in production environments as of 2023, and this number is expected to continue rising. The containerization market has seen a significant uptick, driven by the need for more agile and scalable infrastructure, with a projected growth rate of over 30% annually. As organizations increasingly rely on containerized applications, security concerns around container vulnerabilities, data breaches, and compliance risks have heightened, making container security a top priority for enterprises.
One of the key drivers behind this growth is the wide adoption of container orchestration tools such as Kubernetes, which is now used by more than 85% of organizations. Kubernetes’ popularity has fueled the demand for security solutions that can seamlessly integrate with these platforms. Additionally, reports indicate that over 75% of enterprises consider security integration a crucial factor when selecting container management solutions. This growing emphasis on security has led to the development of specialized container security tools focused on vulnerability scanning, threat detection, and runtime protection.
Despite the increasing adoption of containers, security challenges remain. For instance, studies show that around 30% of container images have high-risk vulnerabilities. This emphasizes the need for continuous monitoring and proactive security measures. As such, over 70% of organizations now include vulnerability scanning in their container security strategy, underlining the importance of ensuring secure containerized applications and infrastructure across the lifecycle.
Key Takeaways
- Market Growth: The global container security market is projected to expand from USD 1.76 billion in 2023 to USD 16.8 billion by 2033, reflecting a significant CAGR of 25.30% over the forecast period.
- Dominant Component: The solution segment holds a leading share of 63.5% in 2023, driven by the increasing demand for comprehensive container security platforms that offer end-to-end protection for containerized applications.
- Cloud Deployment Leadership: Cloud deployment is the preferred model, capturing 56% of the market share in 2023. This dominance is fueled by the growing adoption of cloud-native environments and the need for scalable, flexible security solutions.
- Large Enterprise Focus: The large enterprises segment represents 52% of the market, as larger organizations typically have more complex IT environments and a higher need for robust container security solutions to safeguard their critical workloads.
- IT & Telecom Industry Adoption: The IT & Telecom sector leads the adoption of container security solutions, accounting for 22.5% of the market share, as containerized applications and microservices are widely used to drive digital transformation in this industry.
- Regional Dominance: North America holds the largest regional share at 32% in 2023, driven by the high adoption of cloud computing, containerized applications, and a strong focus on cybersecurity across various industries.
- Revenue Growth Drivers: The increasing use of containerized applications, the shift towards cloud infrastructure, and the rising need for enhanced security in hybrid and multi-cloud environments are key factors driving the rapid growth of the container security market.
By Component
In 2023, the Solution segment held a dominant market position in the container security market, capturing more than 63.5% of the overall market share. This dominance can be attributed to the increasing demand for comprehensive, integrated security solutions that provide end-to-end protection for containerized applications. Containerized environments, particularly in cloud-native and microservices architectures, have become increasingly complex, necessitating advanced solutions that address both the infrastructure and the application layers. The Solution segment includes a variety of security tools such as runtime protection, vulnerability scanning, access controls, and compliance monitoring, all of which are essential for ensuring secure container deployments.
The growing adoption of container technology across industries such as IT, telecom, and retail is a key factor driving the growth of the Solution segment. As organizations continue to deploy containerized applications at scale, there is a heightened need for effective security frameworks that can protect these applications from threats, including data breaches, malicious attacks, and unauthorized access. These solutions also help organizations maintain regulatory compliance, ensuring that security standards are met in industries with stringent data protection regulations, such as finance and healthcare.
The demand for integrated security platforms that can provide centralized management and automation is another reason for the Solution segment’s leading position. Organizations prefer unified security solutions that simplify the complexities of securing container environments, especially in multi-cloud or hybrid-cloud architectures. Furthermore, solutions that offer real-time threat detection and automated remediation capabilities are increasingly sought after, as businesses look to enhance their operational efficiency and security posture.
By Deployment
In 2023, the Cloud deployment segment held a dominant market position, capturing more than 56% of the overall container security market share. This dominance is largely driven by the rapid adoption of cloud-native technologies and the growing preference for flexible, scalable security solutions. As organizations increasingly migrate their workloads to cloud environments, there is a corresponding rise in the demand for cloud-based security solutions that can seamlessly integrate with cloud infrastructure, enabling organizations to secure their containerized applications in dynamic, multi-cloud, and hybrid environments.
The Cloud deployment model offers several key advantages that make it the preferred choice for container security. First, cloud-based solutions provide greater scalability, allowing businesses to easily adapt their security measures as their containerized environments grow. Cloud solutions also enable real-time security updates and automated patches, which are critical in addressing the rapidly evolving threat landscape. As containers are frequently updated and redeployed, the ability to provide continuous security monitoring and automated remediation is a key factor in the growing demand for cloud-based solutions.
Another reason for the dominance of the Cloud segment is the increasing popularity of container orchestration platforms, such as Kubernetes, which are often deployed in cloud environments. These platforms enable the management of containerized applications at scale, and security solutions designed for the cloud offer better integration with these platforms, ensuring that both container workloads and orchestration platforms are effectively secured. Additionally, cloud-based solutions often provide more comprehensive and centralized visibility into security events and vulnerabilities across all containers, making it easier for organizations to maintain a strong security posture.

By Organization Size
In 2023, the Large Enterprises segment held a dominant market position, capturing more than 52% of the overall container security market share. This dominance can be attributed to the larger scale and complexity of operations typically associated with large enterprises, which necessitate robust, scalable security solutions to protect their containerized environments. Large enterprises often manage vast amounts of sensitive data, deploy multiple applications across different environments, and rely on advanced technologies such as microservices and container orchestration platforms. These factors require a higher level of security to safeguard both data and applications against increasingly sophisticated cyber threats.
Large enterprises are more likely to adopt comprehensive container security solutions due to their extensive IT infrastructure and the need to comply with stringent regulatory requirements. With their complex IT ecosystems, large organizations require security solutions that offer centralized management, scalability, and real-time monitoring to ensure that all containers, applications, and systems are protected. The ability to integrate container security solutions with existing enterprise-grade security tools and platforms further drives the adoption of these solutions in large enterprises. Moreover, the increasing adoption of cloud-native technologies and hybrid cloud environments within large organizations contributes significantly to the demand for container security.
Another reason for the large enterprise’s dominance in the market is their ability to allocate more significant resources to cybersecurity initiatives. Large enterprises typically have dedicated security teams, budgets, and technology investments that enable them to implement the latest container security technologies. The adoption of advanced container security solutions such as runtime protection, vulnerability scanning, and compliance monitoring is common among large enterprises, as they strive to protect critical infrastructure and avoid costly breaches.
By Industry Vertical
In 2023, the IT & Telecom segment held a dominant market position, capturing more than 22.5% of the overall container security market share. The significant share of this sector can be attributed to the increasing reliance on digital infrastructure, cloud-based services, and containerized applications within the IT and telecommunications industries. As companies in this sector continue to embrace containerization to streamline their application development and deployment processes, the need for robust container security solutions has surged. The rapid adoption of microservices architectures and container orchestration tools, such as Kubernetes, has made container security a top priority for IT and telecom organizations.
The IT & Telecom industry’s dominance in the container security market is also driven by its massive data flows and high operational complexity. Organizations in this sector manage large-scale networks, databases, and communication systems that require continuous availability and security. The containerization of applications, which enhances scalability and operational efficiency, introduces new vulnerabilities. These risks are further exacerbated by the growing threat landscape, including data breaches, cyberattacks, and insider threats. Therefore, container security solutions that offer real-time monitoring, vulnerability scanning, and threat detection are increasingly critical to protecting sensitive data and ensuring the integrity of network infrastructures.
Moreover, regulatory compliance is a major driver for the adoption of container security solutions in the IT & Telecom sector. With stricter data protection laws such as GDPR in Europe and various other country-specific regulations, organizations in this industry must implement robust security measures to avoid potential penalties and data breaches. Container security technologies that help ensure compliance with these regulatory frameworks are highly sought after. As the sector continues to evolve and innovate, securing containerized environments has become an integral part of the IT & Telecom industry’s cybersecurity strategy.
Key Market Segments
By Component
- Solution
- Services
By Deployment
- Cloud
- On-premise
By Organization Size
- Large enterprises
- Small and medium-sized enterprises
By Industry Vertical
- BFSI
- IT and Telecom
- Retail
- Healthcare
- Manufacturing
- Government
- Others
Driving Factors
Increasing Adoption of Cloud-Native Applications
One of the primary drivers for the growth of the Container Security Market is the increasing adoption of cloud-native applications. As businesses increasingly migrate their workloads to the cloud, they are leveraging technologies like containers and microservices to improve agility, scalability, and efficiency. Containers offer a lightweight and portable environment for deploying applications, making them an ideal solution for companies moving toward a cloud-first strategy.
With the growing reliance on containers, businesses face increased challenges in ensuring the security of their containerized environments. Containers, by design, are inherently more dynamic than traditional virtual machines, which makes them susceptible to a wide range of security threats. This vulnerability has spurred the demand for specialized container security solutions. As containers are deployed across different cloud environments, organizations need solutions that can provide visibility, monitoring, and protection across multi-cloud and hybrid cloud environments.
The rise of DevSecOps (Development, Security, and Operations) practices also plays a significant role in driving demand for container security solutions. DevSecOps encourages the integration of security into the development lifecycle, ensuring that security considerations are addressed at every stage of containerization, from build to deployment. As organizations shift left in their security strategies, container security is becoming an integral part of the DevOps pipeline, contributing to the growing need for security solutions specifically designed for containerized applications.
Restraining Factors
Complexity of Container Security Implementation
While container security solutions are in high demand, the complexity of implementation remains a significant restraint in the market. Container security requires organizations to manage multiple layers of security within a dynamic and distributed environment, which can be challenging for even experienced IT teams. Containerized environments often involve multiple containers, microservices, and orchestration platforms (such as Kubernetes), each of which needs to be secured individually and in combination. This complexity often results in a fragmented security approach, where different solutions are required for different parts of the infrastructure, making it harder for organizations to achieve comprehensive protection.
The container security market is also constrained by the lack of standardized best practices and frameworks. Unlike traditional IT security, which has well-established protocols and tools, container security is still evolving. Organizations need to continuously monitor and update their security protocols to address emerging threats, which can be resource-intensive. Additionally, the constantly changing nature of containerized environments – where containers are spun up and shut down rapidly – makes it difficult to maintain real-time visibility, a crucial component of effective security.
Moreover, the skill gap in managing container security is another barrier. While there is a growing talent pool in the broader cybersecurity industry, container security requires specialized knowledge in both containerization technologies and security practices. This talent gap can hinder the widespread adoption of container security solutions, especially among smaller organizations or businesses that lack the resources to build specialized teams.
Growth Opportunities
Growing Focus on Regulatory Compliance
An emerging opportunity in the container security market is the increasing emphasis on regulatory compliance across industries. With the introduction of data privacy regulations such as the GDPR in the European Union, CCPA in California, and various other data protection laws worldwide, organizations are under greater pressure to secure sensitive data, particularly in cloud environments. Containerized applications, often used to host sensitive data and applications, must comply with these stringent regulations, which creates a strong demand for container security solutions that can help ensure compliance.
Container security plays a critical role in protecting sensitive data within containerized environments. Many regulations require businesses to implement appropriate security controls to prevent data breaches, unauthorized access, and data loss. Containers, by their nature, introduce specific risks related to network vulnerabilities, misconfigurations, and inadequate access controls. As a result, businesses need specialized security measures to address these unique challenges and demonstrate compliance with regulatory frameworks.
Additionally, container security solutions are increasingly being integrated with data encryption, identity management, and audit trail capabilities, all of which are necessary for meeting regulatory requirements. By ensuring that containerized environments adhere to compliance standards, organizations can avoid potential fines, reputational damage, and legal consequences, creating a substantial market opportunity for container security vendors.
Challenging Factors
Evolving Threat Landscape
The evolving threat landscape is one of the most significant challenges facing the container security market today. As containerization continues to grow in popularity, cybercriminals are increasingly targeting containerized environments due to the sensitive data they house and their growing use in mission-critical applications. Containers are particularly vulnerable to security breaches because of their lightweight, highly dynamic nature, which makes it difficult to keep track of each container’s behavior and interactions with other containers.
The rise of sophisticated attacks such as container escapes (where attackers gain access to the host system by exploiting vulnerabilities in the container) and supply chain attacks (targeting vulnerabilities in the container image repositories) further complicates the landscape. Containerized environments are often part of larger microservices architectures that interact with numerous services and applications, increasing the potential attack surface. Securing these environments requires a holistic approach that covers not only the containers themselves but also the orchestration platforms (like Kubernetes), APIs, and network communications involved.
As container security solutions become more advanced, so too do the techniques employed by attackers. Malicious actors are constantly developing new methods to infiltrate containerized systems, forcing security vendors to continuously innovate and improve their offerings. This creates an ongoing challenge for businesses seeking to keep up with emerging threats. The speed at which containers are deployed and removed further complicates threat detection and response. Unlike traditional infrastructure, where systems are static, containers are highly transient, requiring continuous monitoring and rapid response capabilities to mitigate potential attacks.
Growth Factors
The growth of the Container Security Market is being driven by several key factors. Firstly, the increasing adoption of cloud-native applications and microservices architectures by enterprises is contributing to the rapid expansion of container security demand. Containers provide businesses with scalability, efficiency, and portability, making them an integral part of modern application deployment. As more organizations migrate to the cloud and move towards DevOps and DevSecOps practices, the need for robust container security solutions grows.
Another major driver is the rising frequency of cybersecurity threats. Containers, while providing flexibility and speed, also introduce new security challenges due to their lightweight and dynamic nature. These risks have prompted organizations to invest in specialized security solutions that protect containerized environments from vulnerabilities, data breaches, and cyberattacks. The rise in supply chain attacks, targeting vulnerabilities in container image repositories, has further increased the focus on securing containers.
Furthermore, stringent regulatory requirements related to data privacy and security, such as GDPR and CCPA, are compelling organizations to adopt comprehensive container security solutions to ensure compliance. As businesses handle more sensitive data in containerized environments, ensuring that they meet regulatory standards has become a critical concern, further accelerating the market’s growth.
Emerging Trends
In recent years, there has been a noticeable shift toward automated container security solutions. With the increasing complexity of managing containerized environments at scale, organizations are adopting security tools that offer automated vulnerability scanning, continuous monitoring, and threat detection. These tools are designed to identify and mitigate risks in real-time, which is essential in highly dynamic environments like containers.
Another emerging trend is the growing use of AI and machine learning (ML) in container security. By integrating AI and ML technologies, container security solutions are becoming more effective at detecting anomalies, predicting potential threats, and automating security responses. These technologies enable security teams to analyze large volumes of data quickly, identify patterns, and respond to emerging threats faster and more accurately.
In addition, as more organizations embrace multi-cloud and hybrid-cloud environments, the demand for cloud-native security platforms has increased. Container security tools are now being designed to seamlessly integrate with cloud-native infrastructures like Kubernetes, enabling businesses to manage security policies and governance across different cloud providers and on-premise systems. This trend reflects the growing need for security solutions that are both scalable and adaptable to complex, hybrid environments.
Business Benefits
Investing in container security offers a range of business benefits for organizations operating in today’s fast-paced, digital landscape. First and foremost, container security helps ensure business continuity by minimizing the risk of cyberattacks and data breaches. Given that containers are used to host mission-critical applications and sensitive data, securing these environments is vital for maintaining the integrity of the entire business infrastructure. A breach or compromise of containerized systems could lead to severe reputational and financial losses, making container security a top priority for enterprises.
Another significant benefit is the increased agility that robust security solutions provide. As organizations move toward DevSecOps, which integrates security throughout the software development lifecycle, container security solutions allow teams to detect and address vulnerabilities early in the development process. This not only accelerates time-to-market but also reduces the cost and effort associated with fixing security issues post-deployment.
Moreover, container security plays a crucial role in helping organizations achieve regulatory compliance. With strict regulations like GDPR, HIPAA, and CCPA placing greater responsibility on organizations to protect user data, implementing strong container security measures is essential for avoiding legal and financial penalties. Effective container security solutions provide businesses with the tools to ensure that their containerized applications are compliant with these laws, thus reducing the risk of non-compliance and the associated consequences.
Regional Analysis
In 2023, North America held a dominant market position in the Container Security Market, capturing more than a 32% share, with revenue reaching USD 1.04 billion. This region’s leadership can be attributed to several key factors, including the early adoption of containerized applications and advanced cloud infrastructure. North America, particularly the U.S., is home to many large enterprises and technology-driven industries that rely heavily on cloud-native applications and microservices architectures. As these organizations increasingly embrace containerization, the demand for robust container security solutions has grown significantly.
The presence of major tech giants like Amazon, Microsoft, and Google in North America has contributed to a highly developed and competitive market for container security solutions. These companies are at the forefront of cloud innovation, driving the adoption of container technologies across various sectors, including healthcare, finance, and retail. Additionally, North American organizations are increasingly integrating DevSecOps practices into their operations, emphasizing security across the entire development pipeline. This further fuels the demand for automated and comprehensive container security tools, particularly in industries where data protection and regulatory compliance are critical.
North America’s strong regulatory environment also plays a significant role in the market’s dominance. The implementation of stringent data protection regulations such as GDPR, CCPA, and HIPAA has prompted businesses to adopt security measures that ensure compliance. Container security solutions are integral to meeting these regulatory standards, making them a priority for businesses in the region. The growing frequency and sophistication of cyberattacks targeting containerized environments have further reinforced the need for effective security solutions, which has driven both private and public sector investments in cybersecurity.
Key Regions and Countries
- North America
- US
- Canada
- Europe
- Germany
- France
- The UK
- Spain
- Italy
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- India
- Australia
- Singapore
- Rest of Asia Pacific
- Latin America
- Brazil
- Mexico
- Rest of Latin America
- Middle East & Africa
- South Africa
- Saudi Arabia
- UAE
- Rest of MEA
Key Player Analysis
Microsoft Corporation, a dominant player in the Container Security Market, continues to strengthen its position through strategic acquisitions and product innovations. In recent years, Microsoft has heavily invested in container security through its Azure Kubernetes Service (AKS), providing enterprises with tools to secure their containerized applications at scale. The company’s acquisition of Citus Data in 2019 and the subsequent integration of its technology into the Azure cloud platform has enhanced Microsoft’s ability to provide scalable container management and security features.
Broadcom, a leading semiconductor and infrastructure software company, has made notable strides in the container security space through strategic acquisitions. One of the most significant moves was its acquisition of CA Technologies in 2018, which expanded Broadcom’s software portfolio, including solutions for container security. Broadcom’s Symantec Enterprise Cloud Security solutions provide robust protection for cloud-native applications, including containers, helping organizations safeguard their containers in both public and private cloud environments.
IBM, with its rich history in enterprise IT and cybersecurity, has also made substantial investments in the Container Security Market. The company’s Red Hat OpenShift platform, which is designed for managing containerized applications, incorporates robust security features to ensure the integrity and protection of container environments. IBM’s focus on Zero Trust security architecture and integration of container security tools into Red Hat OpenShift provides enterprises with a comprehensive solution to secure applications across multiple clouds and hybrid environments.
Top Key Players in the Market
- Microsoft Corporation
- Broadcom, Inc.
- IBM
- Amazon Web Services
- VMware
- Qualys
- Docker Inc.
- Check Point Software Technologies Ltd.
- Zscaler
- Aqua Security
- Sophos
- Other Key Players
Recent Developments
- In January 2024, Microsoft announced the integration of its Azure Kubernetes Service (AKS) with new container security features, enhancing real-time threat detection and vulnerability management across containerized applications.
- In March 2024, Broadcom Inc. unveiled its upgraded Symantec Cloud Security suite, incorporating advanced container security capabilities designed to secure cloud-native applications.
Report Scope
Report Features Description Market Value (2023) USD 1.76 Bn Forecast Revenue (2033) USD 16.8 Bn CAGR (2024-2033) 25.30% Largest Market North America Base Year for Estimation 2023 Historic Period 2019-2022 Forecast Period 2024-2033 Report Coverage Revenue Forecast, Market Dynamics, Competitive Landscape, Recent Developments Segments Covered By Component (Solution, Services), By Deployment (Cloud, On-premise), By Organization Size (Large enterprises, Small and medium-sized enterprises), By Industry Vertical (BFSI, IT and Telecom, Retail, Healthcare, Manufacturing, Government, Others) Regional Analysis North America (US, Canada), Europe (Germany, UK, Spain, Austria, Rest of Europe), Asia-Pacific (China, Japan, South Korea, India, Australia, Thailand, Rest of Asia-Pacific), Latin America (Brazil), Middle East & Africa(South Africa, Saudi Arabia, United Arab Emirates) Competitive Landscape Microsoft Corporation, Broadcom, Inc., IBM, Amazon Web Services, VMware, Qualys, Docker Inc., Check Point Software Technologies Ltd., Zscaler, Aqua Security, Sophos, Other Key Players Customization Scope We will provide customization for segments and at the region/country level. Moreover, additional customization can be done based on the requirements. Purchase Options We have three licenses to opt for: Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited User and Printable PDF) 
-
-
- Microsoft Corporation
- Broadcom, Inc.
- IBM
- Amazon Web Services
- VMware
- Qualys
- Docker Inc.
- Check Point Software Technologies Ltd.
- Zscaler
- Aqua Security
- Sophos
- Other Key Players












