Global Intrinsic Security Market Size, Share and Analysis Report By Component (Hardware , Software, Services), By Security Type (Hardware-based Security), By Deployment Mode (On-premises, Cloud-based), By Organization Size (Large Enterprises, Small and Medium-sized Enterprises), By End-User Industry (Banking, Financial Services, and Insurance, Government and Defense,Others), By Regional Analysis, Global Trends and Opportunity, Future Outlook By 2025-2035
- Published date: Jan. 2026
- Report ID: 174260
- Number of Pages: 360
- Format:
-
keyboard_arrow_up
Quick Navigation
- Report Overview
- Top Market Takeaways
- Component Analysis
- Security Type Analysis
- Deployment Mode Analysis
- Organization Size Analysis
- End-User Industry Analysis
- Emerging Trends
- Growth Factors
- Key Market Segments
- Regional Analysis
- Driver Analysis
- Restraint Analysis
- Opportunity Analysis
- Challenge Analysis
- Competitive Analysis
- Future Outlook
- Recent Developments
- Report Scope
Report Overview
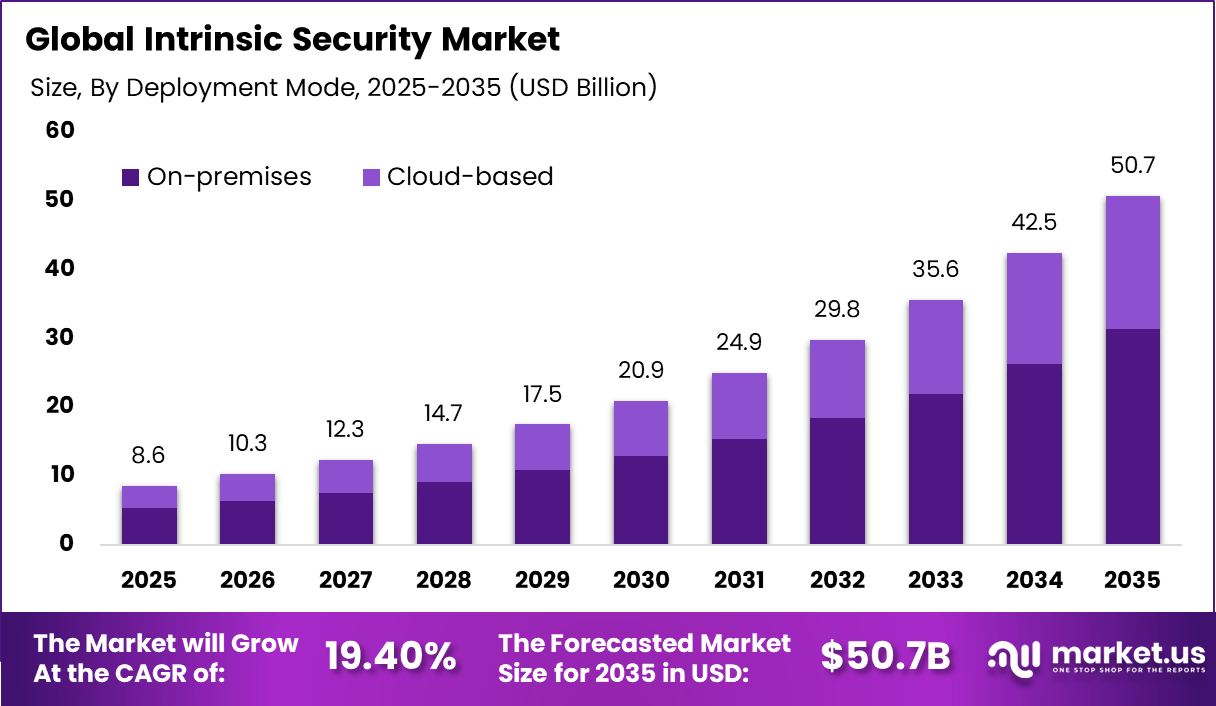
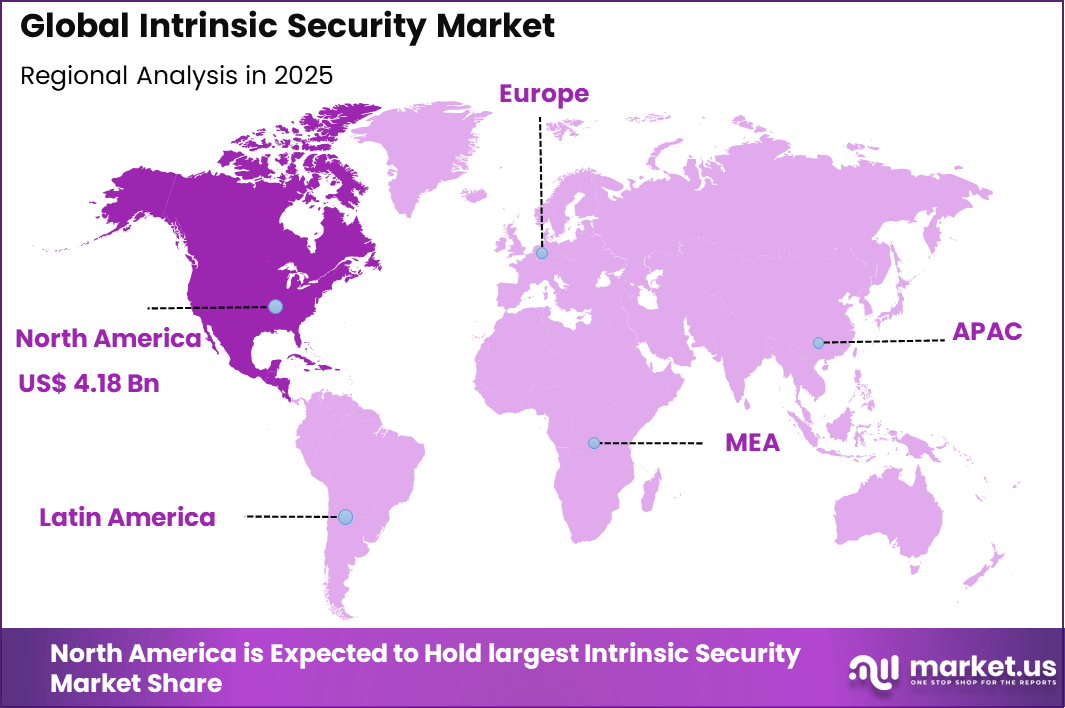
The Global Intrinsic Security Market generated USD 8.6 billion in 2025 and is predicted to register growth from USD 10.3 billion in 2026 to about USD 50.7 billion by 2035, recording a CAGR of 19.40% throughout the forecast span. In 2025, North America held a dominan market position, capturing more than a 48.6% share, holding USD 4.18 Billion revenue.
The intrinsic security market refers to security technologies that are embedded directly into hardware, software, networks, or systems by design. These solutions protect systems at their core rather than relying only on external security layers. Intrinsic security focuses on identity, access control, encryption, and integrity built into system architecture. It is applied across cloud platforms, enterprise IT systems, connected devices, and digital infrastructure. Adoption supports stronger protection against modern cyber threats.
One major driving factor of the intrinsic security market is the rise in sophisticated cyber attacks. Threat actors increasingly target system vulnerabilities at the application and hardware level. Embedded security reduces exposure to such attacks. Built-in protection improves system resistance. This need drives adoption across industries. Another key driver is the expansion of cloud and connected systems. Cloud platforms, remote work, and connected devices increase security complexity.
Demand for intrinsic security solutions is influenced by growing digital transformation initiatives. Organizations embed security into systems to reduce operational risk. Security-by-design approaches improve long-term protection. This proactive stance increases adoption. Demand remains strong across sectors. It is also shaped by compliance and risk management priorities. Organizations must protect sensitive data and critical systems.
Top Market Takeaways
- By component, hardware led the intrinsic security market with 58.3% share, providing embedded protection directly within devices for tamper-resistant operations.
- By security type, hardware-based security captured 52.7%, offering root-of-trust capabilities against sophisticated cyber threats.
- By deployment mode, on-premises solutions dominated at 61.8%, favored for maximum control and data sovereignty in sensitive environments.
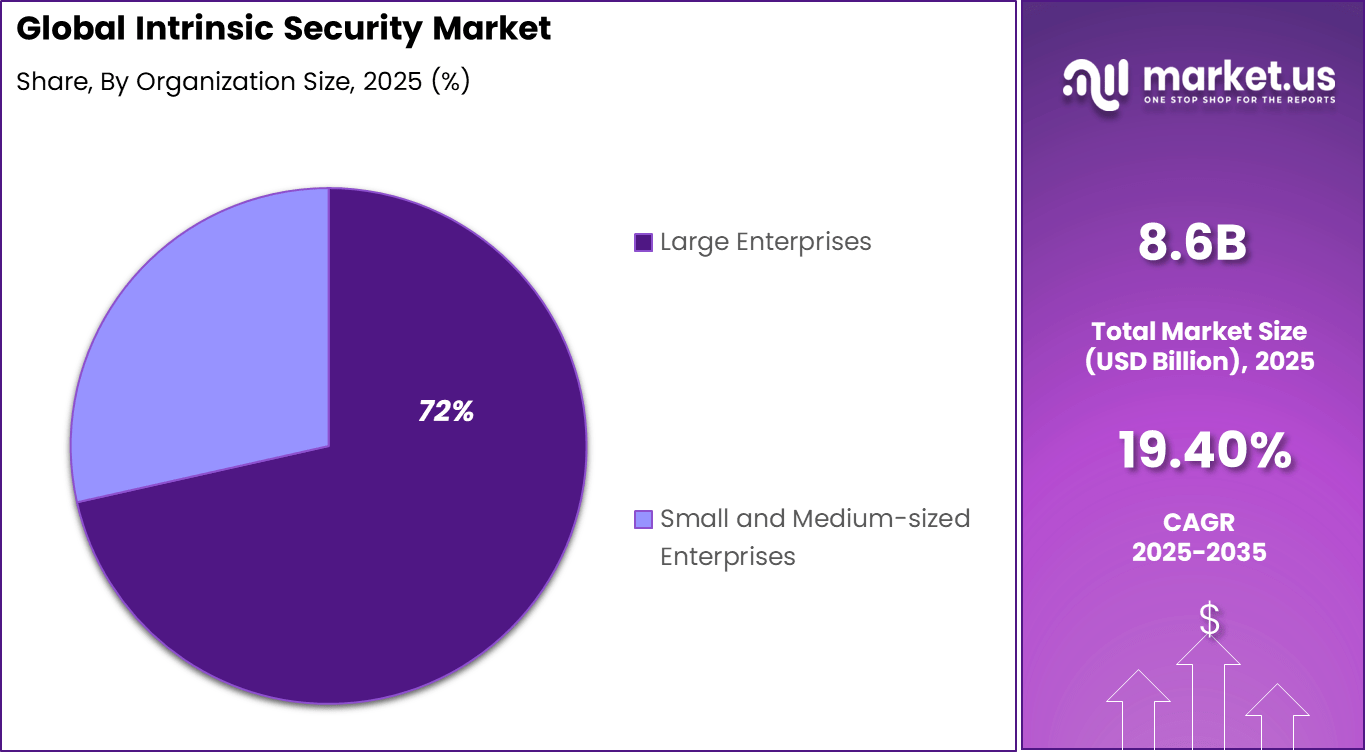
- By organization size, large enterprises accounted for 71.5%, implementing intrinsic security across extensive IT infrastructures.
- By end-user industry, banking, financial services, and insurance held 34.8%, prioritizing hardware-rooted defenses for transaction integrity.
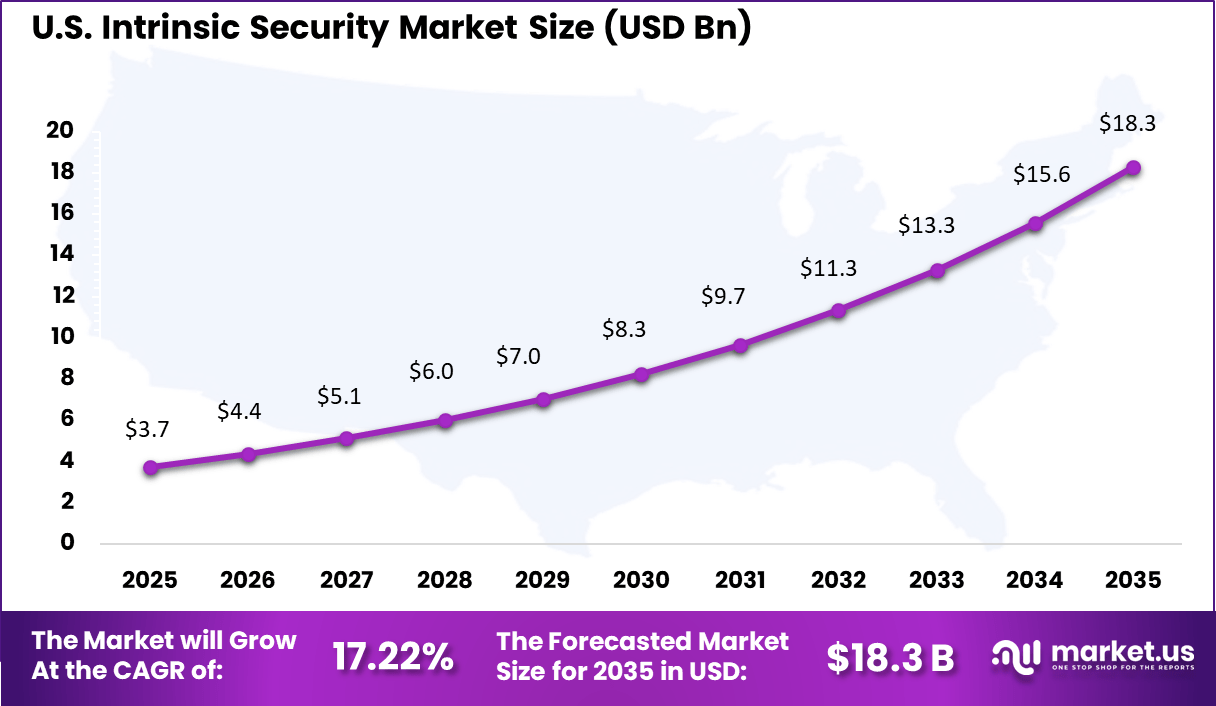
- North America represented 48.6% of the global market, with the U.S. valued at USD 3.73 billion and growing at a CAGR of 17.22%.
Component Analysis
Hardware accounts for 58.3%, highlighting its critical role in intrinsic security architectures. Hardware-based components embed security directly into devices and systems. This approach reduces reliance on external software layers. Embedded security improves resistance to tampering and unauthorized access. Reliability remains a core requirement for secure environments.
The dominance of hardware components is driven by the need for foundational protection. Organizations prefer security that is built into physical infrastructure. Hardware-based security supports long-term system integrity. It also operates independently of application-level vulnerabilities. This sustains strong demand for hardware components.
Security Type Analysis
Hardware-based security represents 52.7%, making it the leading security type. This approach integrates security mechanisms directly into chips and devices. It supports secure boot, encryption, and identity protection. Hardware-level controls reduce attack surfaces. Protection remains consistent throughout the system lifecycle.
Adoption of hardware-based security is driven by rising threat complexity. Software-only controls are often insufficient. Hardware-based methods provide stronger trust anchors. Organizations value persistent protection. This keeps hardware-based security widely adopted.
Deployment Mode Analysis
On-premises deployment holds 61.8%, reflecting preference for local control. Sensitive data remains within internal environments. On-premises systems support strict compliance requirements. Predictable performance improves reliability. Organizations maintain full oversight of security infrastructure.
The dominance of on-premises deployment is driven by regulatory and privacy concerns. Many enterprises operate in highly regulated sectors. Local deployment allows customization of security controls. Reduced dependency on external networks improves assurance. This sustains strong on-premises adoption.
Organization Size Analysis
Large enterprises account for 71.5%, making them the primary adopters of intrinsic security. These organizations manage complex and distributed systems. Embedded security supports consistent protection across assets. Large enterprises prioritize resilience and continuity. Scale increases exposure to risks.
Adoption among large enterprises is driven by operational complexity. Security must be integrated at the infrastructure level. Intrinsic security reduces management overhead. Centralized governance improves control. This sustains strong enterprise-level demand.
End-User Industry Analysis
The banking, financial services, and insurance sector represents 34.8%, making it a key end-user industry. This sector handles highly sensitive financial data. Intrinsic security supports transaction integrity and data protection. Embedded controls reduce fraud risk. Compliance remains a top priority.
Growth in this sector is driven by regulatory pressure. Financial institutions require strong foundational security. Hardware-based controls support audit readiness. Secure infrastructure builds customer trust. This sustains steady adoption in BFSI.
Emerging Trends
Key Trend Description AI-powered threat prediction Machine learning anticipates attacks using behavioral baselines. Zero-trust architecture expansion Continuous verification across all assets and users. Hardware-rooted security Chip-level protections prevent firmware exploits. Privacy-enhancing technologies Homomorphic encryption for secure data processing. Autonomous response systems Self-healing networks isolate breaches instantly. Growth Factors
Key Factors Description Sophisticated cyber threats Ransomware and supply chain attacks demand built-in defenses. Cloud and hybrid adoption Distributed environments require embedded security. Regulatory compliance pressures GDPR and similar laws enforce intrinsic controls. IoT proliferation Billions of devices need inherent protection. Digital transformation scale Enterprises prioritize security-by-design in operations. Key Market Segments
By Component
- Hardware
- Secure Processors & Chips
- Trusted Platform Modules
- Hardware Security Modules
- Others
- Software
- Firmware & BIOS Security
- Secure Operating Systems
- Security Management Platforms
- Others
- Services
- Consulting & Integration
- Support & Maintenance
- Managed Services
- Others
By Security Type
- Hardware-based Security
- Software-based Security
- Chip-level Security
By Deployment Mode
- On-premises
- Cloud-based
By Organization Size
- Large Enterprises
- Small and Medium-sized Enterprises
By End-User Industry
- Banking, Financial Services, and Insurance
- Government & Defense
- Healthcare
- IT & Telecommunications
- Manufacturing
- Others
Regional Analysis
North America accounted for 48.6% share, supported by strong focus on secure by design principles across enterprise IT and industrial systems. Intrinsic security approaches, which embed protection directly into hardware, software, and network architectures, have been widely adopted to reduce attack surfaces and improve system resilience.
Demand has been driven by increasing cyber threats, complexity of digital infrastructure, and stricter regulatory requirements. Organizations in the region have prioritized intrinsic security to move beyond reactive security models and build protection into core system design.
The U.S. market reached USD 3.73 Bn and is projected to grow at a 17.22% CAGR, reflecting strong investment in advanced cybersecurity architectures. Adoption has been particularly high in critical infrastructure, defense, finance, and technology sectors, where embedded security is essential for reliability and compliance. Intrinsic security has helped U.S. organizations reduce vulnerabilities, improve system integrity, and strengthen trust in digital platforms.
Key Regions and Countries
- North America
- US
- Canada
- Europe
- Germany
- France
- The UK
- Spain
- Italy
- Russia
- Netherlands
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- India
- Australia
- Singapore
- Thailand
- Vietnam
- Rest of APAC
- Latin America
- Brazil
- Mexico
- Rest of Latin America
- Middle East & Africa
- South Africa
- Saudi Arabia
- UAE
- Rest of MEA
Driver Analysis
The intrinsic security market is being driven by the growing urgency to embed security directly within digital operations rather than relying solely on perimeter-based defenses. Organisations face increasingly sophisticated threats that target applications, data, and infrastructure at multiple layers, necessitating a security approach that is continuous, pervasive, and context-aware.
Intrinsic security frameworks integrate protection, detection, and response capabilities throughout the enterprise technology stack, enabling real-time visibility and automated threat mitigation across networks, cloud environments, and endpoints.
The rise of distributed workforces, cloud adoption, and hybrid IT architectures has amplified exposure to cyber risks, reinforcing demand for intrinsic security measures that can adapt dynamically to evolving threat landscapes.
Restraint Analysis
A significant restraint in the intrinsic security market arises from the complexity and resource requirements associated with implementation and management. Organisations must harmonise security telemetry, identity data, access policies, and automation tools across diverse environments to realise intrinsic security benefits, which can demand extensive planning and specialised expertise.
Integrating intrinsic security solutions with legacy systems, disparate security controls, and organisational processes often introduces technical and operational friction. These integration challenges can slow deployment timelines and increase total cost of ownership, particularly for entities with limited security maturity or constrained cybersecurity budgets.
Opportunity Analysis
Emerging opportunities in the intrinsic security market are linked to the acceleration of digital transformation and the expanding threat surface associated with cloud, mobile, and Internet of Things deployments. As enterprises prioritise resilient application delivery and secure user experiences, security capabilities that are native to development lifecycles and runtime environments can offer strategic value.
Intrinsic security supports DevSecOps practices by embedding security automation into continuous integration and delivery pipelines, enabling rapid identification and remediation of vulnerabilities. Solutions that offer adaptive response, behavioural analytics, and real-time risk scoring also open possibilities for proactive defence and operational insight across hybrid infrastructure.
Challenge Analysis
A central challenge confronting the intrinsic security market relates to balancing the demands of automation and contextual accuracy with user trust and operational transparency. Automated security response mechanisms must be finely calibrated to avoid over-reliance on algorithmic decisions while ensuring timely mitigation of genuine threats.
False positives and unclear alerts can erode confidence in intrinsic security tools and burden security teams with unnecessary investigations. Furthermore, ensuring consistent policy enforcement and unified incident response across on-premises, cloud, and remote environments requires robust governance frameworks and cross-functional collaboration.
Competitive Analysis
Intel Corporation, Advanced Micro Devices, Inc., ARM Holdings plc, Qualcomm Incorporated, and NVIDIA Corporation lead the intrinsic security market by embedding security features directly into processors, chipsets, and hardware architectures. Their technologies enable secure boot, trusted execution environments, and hardware based isolation. These capabilities are critical for protecting devices against firmware level and physical attacks.
International Business Machines Corporation, Microsoft Corporation, Google LLC, Cisco Systems, Inc., and Hewlett Packard Enterprise Company strengthen the market by integrating intrinsic security into servers, operating systems, cloud platforms, and networking infrastructure. Their solutions focus on zero trust architectures, secure hardware roots, and continuous threat protection.
Dell Technologies, Inc., Thales Group, Infineon Technologies AG, STMicroelectronics N.V., and Microchip Technology Inc. expand the landscape with secure elements, hardware encryption, and trusted identity solutions. Their offerings support automotive, industrial, and IoT security requirements. These companies focus on compliance, reliability, and long product lifecycles.
Top Key Players in the Market
- Intel Corporation
- Advanced Micro Devices, Inc.
- ARM Holdings plc
- Qualcomm Incorporated
- NVIDIA Corporation
- International Business Machines Corporation
- Microsoft Corporation
- Google LLC
- Cisco Systems, Inc.
- Hewlett Packard Enterprise Company
- Dell Technologies, Inc.
- Thales Group
- Infineon Technologies AG
- STMicroelectronics N.V.
- Microchip Technology Inc.
- Others
Future Outlook
Growth in the Intrinsic Security market is expected to remain strong as organizations embed security directly into systems and applications. Instead of adding security as a separate layer, intrinsic security focuses on protection at the design and architecture level.
Rising cyber threats and complex digital environments are supporting this shift. Over time, wider adoption of secure by design practices, automation, and integration with development workflows is likely to improve overall system resilience.
Recent Developments
- Intel boosted vPro Security at CES 2025, tackling 150+ MITRE attacks with hardware validations for AI PCs, plus advisories in May and August 2025.
- ARM saw solid growth in 2025 from licensing its designs for AI chips. The company enjoyed a 33% stock rise tied to new partnerships. Their Neoverse cores provide embedded security for edge devices.
Report Scope
Report Features Description Market Value (2025) USD 8.6 Bn Forecast Revenue (2035) USD 50.70 Bn CAGR(2025-2035) 19.40% Base Year for Estimation 2024 Historic Period 2020-2024 Forecast Period 2025-2035 Report Coverage Revenue forecast, AI impact on Market trends, Share Insights, Company ranking, competitive landscape, Recent Developments, Market Dynamics and Emerging Trends Segments Covered By Component (Hardware (Secure Processors and Chips,Trusted Platform Modules,Others),Software (Firmware and BIOS Security,Secure Operating Systems,Others),Services (Consulting and Integration,Support and Maintenance,Others)), By Security Type (Hardware-based Security), By Deployment Mode (On-premises,Cloud-based), By Organization Size (Large Enterprises,Small and Medium-sized Enterprises), By End-User Industry (Banking, Financial Services, and Insurance,Government and Defense,Others) Regional Analysis North America – US, Canada; Europe – Germany, France, The UK, Spain, Italy, Russia, Netherlands, Rest of Europe; Asia Pacific – China, Japan, South Korea, India, New Zealand, Singapore, Thailand, Vietnam, Rest of Latin America; Latin America – Brazil, Mexico, Rest of Latin America; Middle East & Africa – South Africa, Saudi Arabia, UAE, Rest of MEA Competitive Landscape Intel Corporation, Advanced Micro Devices, Inc., ARM Holdings plc, Qualcomm Incorporated, NVIDIA Corporation, International Business Machines Corporation, Microsoft Corporation, Google LLC, Cisco Systems, Inc., Hewlett Packard Enterprise Company, Dell Technologies, Inc., Thales Group, Infineon Technologies AG, STMicroelectronics N.V., Microchip Technology Inc., Others Customization Scope Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements. Purchase Options We have three license to opt for: Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited User and Printable PDF) 
-
-
- Intel Corporation
- Advanced Micro Devices, Inc.
- ARM Holdings plc
- Qualcomm Incorporated
- NVIDIA Corporation
- International Business Machines Corporation
- Microsoft Corporation
- Google LLC
- Cisco Systems, Inc.
- Hewlett Packard Enterprise Company
- Dell Technologies, Inc.
- Thales Group
- Infineon Technologies AG
- STMicroelectronics N.V.
- Microchip Technology Inc.
- Others










