Global Threat Deception Platform Market Size, Share, Industry Analysis Report By Component (Software, Services(Professional Services, Managed Services)) By Deployment Mode (Cloud-based, On-Premises) By Deception Stack (Network Deception, Endpoint Deception,Others) By Organization Size(Large Enterprises, Small and Medium-sized Enterprises (SMEs)) By End-User(Banking, Financial Services, and Insurance (BFSI), Others) By Regional Analysis, Global Trends and Opportunity, Future Outlook By 2025-2034
- Published date: Dec.2025
- Report ID: 168716
- Number of Pages: 384
- Format:
-
keyboard_arrow_up
Quick Navigation
- Report Overview
- Top Market Takeaways
- By Component
- By Deployment Mode
- By Deception Stack
- By Organization Size
- By End-User
- Key Reasons for Adoption
- Benefits
- Usage Trends
- Emerging Trends
- Growth Factors
- Key Market Segments
- Regional Analysis
- Driver
- Restraint
- Opportunity
- Challenge
- Competitive Analysis
- Future Outlook
- Recent Developments
- Report Scope
Report Overview
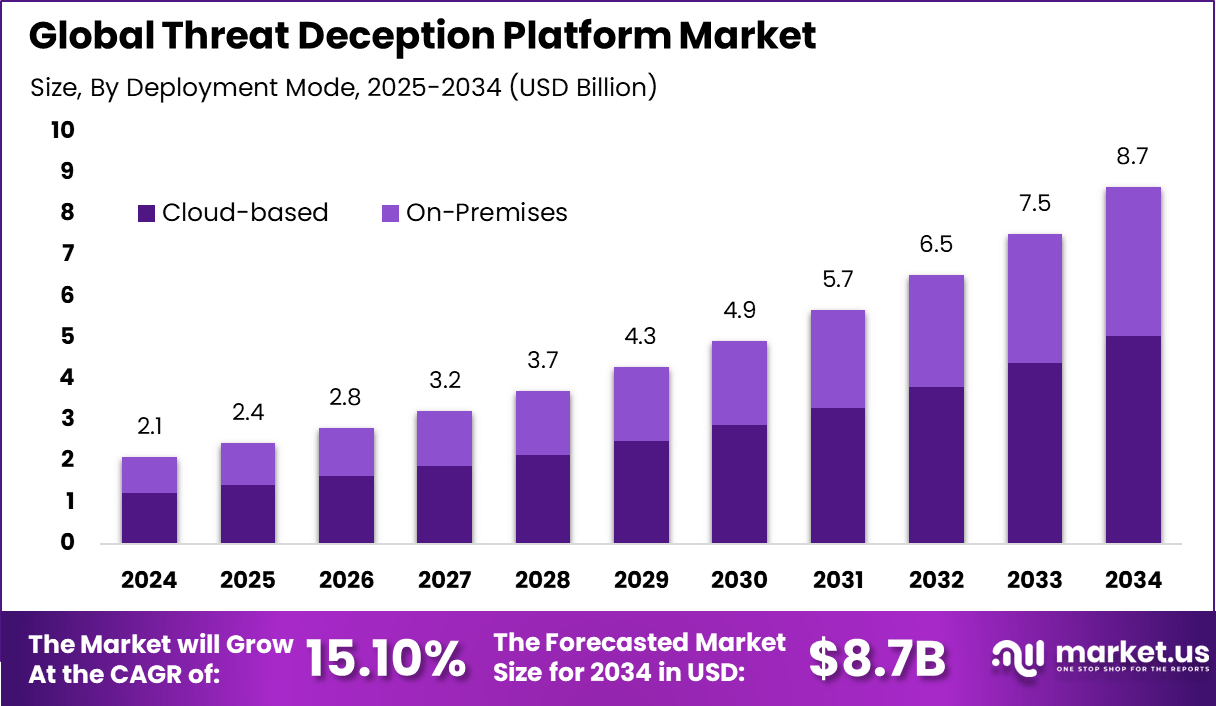
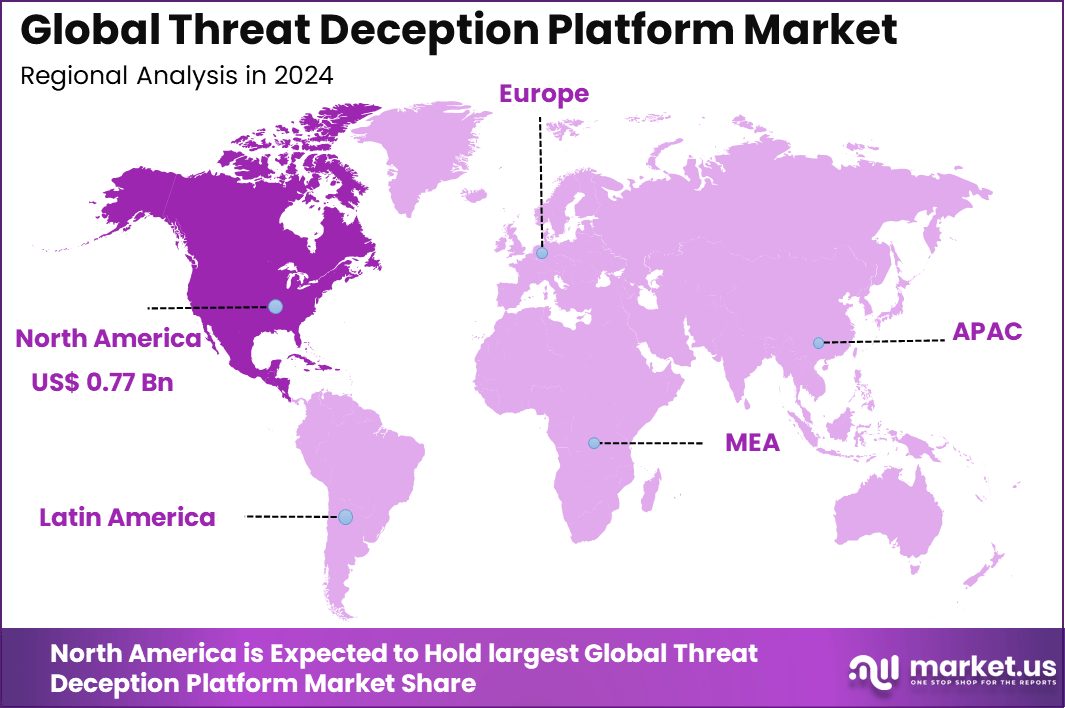
The Global Threat Deception Platform Market generated USD 2.1 billion in 2024 and is predicted to register growth from USD 2.4 billion in 2025 to about USD 8.7 billion by 2034, recording a CAGR of 15.10% throughout the forecast span. In 2024, North America held a dominan market position, capturing more than a 36.4% share, holding USD 0.77 Billion revenue.
The threat deception platform market has expanded as organisations adopt proactive cybersecurity tools designed to mislead attackers and identify intrusions before they reach critical systems. Growth reflects rising sophistication of cyberattacks, increasing reliance on digital infrastructure and the need for early detection capabilities. Threat deception platforms now support enterprises, government agencies and critical infrastructure operators seeking stronger defensive depth.
The growth of the market can be attributed to increasing attack complexity, rising incidents of credential theft and stronger demand for real time visibility into lateral movement. Traditional security tools often miss advanced threats that bypass perimeter controls. Deception techniques create decoys, traps and false assets that lure intruders into monitored environments, improving detection accuracy and reducing dwell time.
Demand is rising across financial institutions, healthcare providers, energy companies, manufacturing facilities and cloud driven enterprises. Organisations operating in regulated sectors adopt deception tools to meet stringent security expectations and enhance audit readiness. Companies with distributed networks and remote operations use deception platforms to monitor suspicious activity across multiple environments. Growth is particularly strong in regions with high cybersecurity maturity.
Top Market Takeaways
- By component, software leads with 64.1% share, including platforms that deploy decoys, breadcrumbs, and traps across networks, endpoints, and cloud environments to detect and mitigate cyber threats proactively.
- By deployment mode, cloud-based solutions hold 58.3% share, favored for scalability, ease of integration, and cost-effective management of complex IT environments spanning hybrid and multi-cloud infrastructures.
- By deception stack, network deception is prominent with 30.8% share, protecting critical network assets by luring attackers into decoy environments to detect and isolate threats before damage occurs.
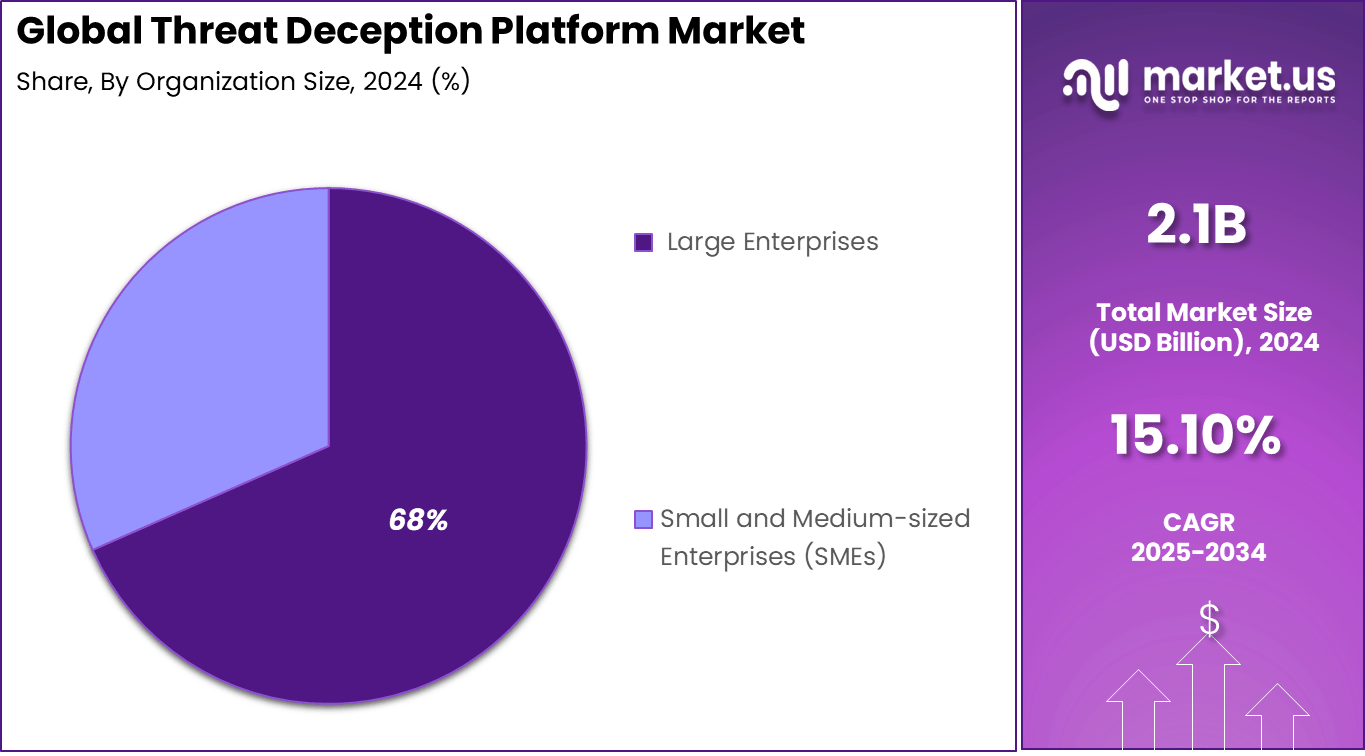
- By organization size, large enterprises dominate with 68.4% share, driven by complex cybersecurity needs, stringent compliance requirements, and significant investments in proactive threat detection technologies.
- By end-user, BFSI holds 26% share due to the sector’s high exposure to cyber threats, stringent regulatory oversight, and need for robust platforms to protect sensitive financial data and ensure operational resilience.
- Regionally, North America accounts for approximately 36.4% market share.
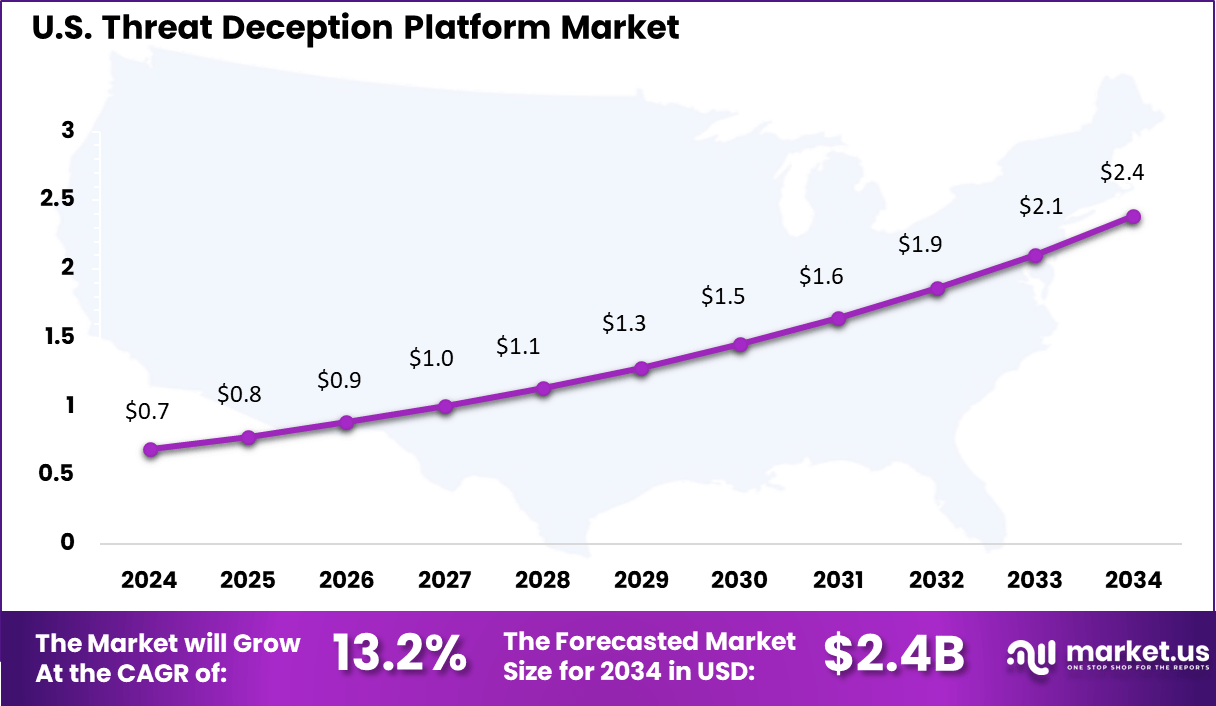
- The U.S. market size is estimated at around USD 0.69 billion in 2025.
- The market is growing at a CAGR of 13.2%, fueled by rising cyberattacks, adoption of zero-trust architectures, integration with SIEM/SOAR platforms, and AI-driven analytics enhancing detection accuracy and response speed.
By Component
Software forms the backbone of the threat deception platform market, accounting for a dominant 64.1% share. These software solutions deploy decoys, traps, and honeytokens that confuse attackers and divert threats away from critical assets.
They offer real-time monitoring, analytics, and automated incident responses to detect and neutralize cyber intrusions effectively. The continuous evolution in deception algorithms enhances the ability to mimic genuine network activity, making attackers difficult to distinguish from legitimate users.
Increased integration with SIEM and SOAR platforms amplifies threat visibility and accelerates response times. Enterprises prioritize software owing to its flexibility, scalability, and ability to update rapidly against emerging threats without costly hardware changes, positioning it as a critical layer in modern cybersecurity frameworks.
By Deployment Mode
Cloud-based deployment captures 58.3% of the market as organizations shift to scalable, cost-efficient security solutions that support remote work and hybrid cloud architectures. Cloud platforms enable swift deployment of deception capabilities globally, making it easier to maintain decoy systems across distributed enterprise environments. These deployments reduce upfront investments and facilitate continuous updates to counter sophisticated attacks.
The cloud’s inherent agility aids in managing complex security operations without increasing internal overhead. Companies benefit from centralized dashboards and analytics, aggregating data from multiple endpoints to form a cohesive defense, especially as cloud adoption accelerates in cybersecurity ecosystems.
By Deception Stack
Network deception accounts for 30.8% of the threat deception platform market, serving as a core component in early threat detection and containment. This stack creates realistic decoy environments within network traffic to lure attackers, preventing lateral movement and minimizing damage.
Network deception gives security teams enhanced visibility into attacker behaviors and tactics, enabling more precise and proactive intervention before breaches escalate. This focus on network security reflects the critical need to protect enterprise data flows since network infrastructure often serves as the attack gateway. Growing adoption of IoT and cloud computing elevates network complexity, reinforcing the demand for advanced network deception technologies.
By Organization Size
Large enterprises dominate with a 68.4% share, driven by their complex infrastructures, sizable attack surfaces, and significant cybersecurity budgets. These organizations adopt threat deception platforms to proactively detect advanced persistent threats targeting sensitive data and intellectual property. Large enterprises benefit from comprehensive platform functionalities that support threat intelligence sharing, automated response, and compliance with stringent regulatory requirements.
The competitive pressure to reduce breach impact and reputational damage further fuels investment in deception technologies. Large organizations prioritize integration with existing security tools and scalable automation capabilities to strengthen their layered defense postures.
By End-User
The banking, financial services, and insurance (BFSI) sector forms 26% of the threat deception platform market. This industry faces relentless cyberattacks due to the sensitivity and regulatory nature of financial data. Threat deception platforms provide BFSI firms with early incident detection, fraud prevention, and enhanced regulatory compliance. The ability to detect sophisticated attacks and insider threats using decoy assets helps maintain customer trust and business continuity.
Growing digital transformation in BFSI, including mobile banking and fintech innovations, expands the attack surface, increasing reliance on adaptive security solutions like deception platforms. BFSI organizations drive technology adoption to stay ahead in an evolving threat landscape while safeguarding critical financial infrastructure.
Key Reasons for Adoption
- The rise of sophisticated cyberattacks and AI-driven threats pushes organizations to adopt threat deception platforms for proactive defense instead of just reactive security.
- Growing concern over insider threats and identity-based attacks motivates firms to deploy deception technology that can detect and thwart these hidden risks.
- Integration with existing security systems like SIEM, XDR, and SOAR makes deception platforms attractive for boosting real-time threat intelligence and incident response.
- Compliance and regulatory demands in sectors like finance, healthcare, and government require heightened security with detailed audit trails available from deception platforms.
- Cloud and IoT expansions increase attack surfaces, making automated deception environments essential for comprehensive protection.
Benefits
- Early threat detection through decoy assets triggers alerts immediately when attackers engage, enabling fast incident response before real damage occurs.
- High accuracy in detection reduces false positives, allowing security teams to focus on genuine threats and reduce alert fatigue.
- Threat intelligence enrichment provides insights into attacker techniques and behaviors, helping organizations strengthen defenses based on real attacker data.
- Deception platforms divert attackers away from real assets, protecting critical systems and reducing risk exposure.
- Automation and AI integration support scaling of defenses and adaptive responses, reducing manual management overhead.
Usage Trends
- Adoption is growing in financial services, healthcare, and government, where sensitive data requires advanced protection and compliance.
- Real-time automated response workflows tied to deception alerts are increasingly common, allowing faster mitigation with less human intervention.
- Expansion of deception to IoT and hybrid cloud environments to cover broader attack surfaces reflects evolving enterprise infrastructure.
- Increasing use of behavioral analytics and machine learning to detect anomalies and suspicious behavior within deceptive environments.
- Security operations centers leverage deception platforms to reduce false alerts, gain richer context on attacks, and validate incident response procedures.
Emerging Trends
Key Trends Description AI and Machine Learning Integration Use of AI-powered analytics for real-time threat intelligence, behavioral modeling, and automated response. Integration with Extended Detection and Response (XDR) Seamless integration with XDR, SIEM, and zero-trust frameworks to enhance detection and incident response. Cloud and SaaS Deployment Models Shift to cloud-based platforms for scalability, centralized management, and faster updates. Automation and Orchestration Automated deception deployment, alerting, and incident remediation to reduce response times and false positives. Industry-Specific Deception Solutions Customized platforms for sectors like BFSI, healthcare, government, and telecom with tailored threat scenarios. Growth Factors
Key Factors Description Rising Sophistication of Cyber Threats Increasingly complex cyberattacks driving adoption of proactive threat detection technologies. Regulatory Compliance Demands Stricter data protection laws and cybersecurity regulations accelerating investment in deception platforms. Growth of Remote Work and IoT Devices Expanded attack surfaces requiring adaptive endpoint and network deception capabilities. Government Initiatives and Funding National cybersecurity strategies and grants boosting market growth, especially in critical sectors. Increased Awareness of Proactive Cybersecurity Organizations prioritizing early detection and threat hunting to minimize breach impact and costs. Key Market Segments
By Component
- Software
- Services
- Professional Services
- Managed Services
By Deployment Mode
- Cloud-based
- On-Premises
By Deception Stack
- Network Deception
- Endpoint Deception
- Application Deception
- Data Deception
- Active Directory (AD) Deception
By Organization Size
- Large Enterprises
- Small and Medium-sized Enterprises (SMEs)
By End-User
- Banking, Financial Services, and Insurance (BFSI)
- IT & Telecommunications
- Government & Defense
- Healthcare & Life Sciences
- Retail & E-commerce
- Energy & Utilities
- Others
Regional Analysis
North America dominated the threat deception platform market with a 36.4% global share, driven by escalating cyber threats and early adoption of advanced cybersecurity measures among enterprises and government organizations. The region’s leadership stems from substantial investments in deception technologies that deploy decoys to mislead attackers, providing early threat detection and enhanced incident response capabilities.
Mature IT ecosystems and stringent data protection regulations accelerate deployment across sectors like finance, healthcare, and defense, where real-time analytics and AI integration offer superior visibility into attack patterns. North America’s concentration of leading vendors and cybersecurity innovation hubs solidifies its position as the primary market for threat deception solutions.
The U.S. leads within North America, valued at USD 0.69 billion in 2024 and growing at a CAGR of 13.2%, fueled by high-profile breaches prompting proactive defenses through deception platforms. U.S. organizations prioritize these tools for their ability to complement traditional security stacks, enabling faster threat hunting and reduced dwell time for adversaries.
Government initiatives and enterprise focus on Zero Trust architectures further boost adoption, with providers enhancing features like automated decoy generation and behavioral analytics. This dynamic positions the U.S. as the core growth driver, influencing global standards in threat deception technology.
Key Regions and Countries
- North America
- US
- Canada
- Europe
- Germany
- France
- The UK
- Spain
- Italy
- Russia
- Netherlands
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- India
- Australia
- Singapore
- Thailand
- Vietnam
- Rest of APAC
- Latin America
- Brazil
- Mexico
- Rest of Latin America
- Middle East & Africa
- South Africa
- Saudi Arabia
- UAE
- Rest of MEA
Driver
Escalating Sophisticated Cyber Threats
The threat deception platform market grows from the surge in advanced cyberattacks like ransomware and zero-day exploits that bypass traditional defenses. These platforms deploy realistic decoys and traps to lure attackers early, providing real-time intelligence before damage occurs. This proactive approach appeals to organizations tired of reactive security that fails against persistent threats.
Rising insider risks and social engineering attacks further boost demand, as deception tools monitor lateral movement and anomalous behavior effectively. Sectors like finance and healthcare adopt them to safeguard critical data amid intensifying threats.
Restraint
Difficult deployment and integration
Adoption is limited by the operational difficulty involved in setting up and managing deception platforms. Many enterprises run a mix of legacy infrastructure, on-premise systems, cloud workloads, and multiple endpoint environments.
Integrating deception elements into such diverse systems often takes time and requires trained specialists. This makes deployment slower and increases both cost and effort. These concerns create hesitation among organizations that lack internal expertise for complex security implementations.
Opportunity
Expansion of digital systems and connected devices
The rising use of cloud services, remote work solutions, connected devices, and distributed applications is creating new opportunities for deception platforms. As digital environments grow, the attack surface becomes larger and more complex, which increases the need for early detection.
Threat deception platforms can be deployed across networks, endpoints, applications, and cloud infrastructure to provide stronger visibility into suspicious activity. Companies that are expanding their digital operations are showing greater interest in adopting deception tools to protect their environments more effectively.
Challenge
Low awareness and shortage of skilled professionals
A key challenge for the market is limited awareness about how deception technology works. Many organizations are still unfamiliar with its benefits or consider it an advanced tool suited mainly for large enterprises.
In addition, the shortage of skilled cybersecurity professionals makes it harder for companies to manage deception systems and analyze the activity they capture. Without skilled staff, organizations may struggle to understand alerts or use the technology to its full potential, which slows wider adoption.
Competitive Analysis
Attivo Networks, TrapX Security, Illusive Networks, and Smokescreen Technologies lead the threat deception platform market with advanced tools that deploy decoys, lures, and fake assets to mislead attackers. Their platforms focus on early breach detection, lateral movement tracking, and high-fidelity alerts. These companies help enterprises strengthen threat visibility and reduce dwell time.
Acalvio Technologies, Cymmetria, Guardicore, Allure Security, Fidelis Cybersecurity, Rapid7, and LogRhythm strengthen the competitive landscape with integrated deception frameworks that blend analytics, endpoint visibility, and automated response. Their solutions support SOC teams with real-time attacker behavior insights and low-noise alerting. These providers emphasize scalability, hybrid-cloud deployment, and seamless integration with existing security stacks.
CounterCraft, CyberTrap, and other participants expand the market with specialized deception engines tailored for mid-sized enterprises and targeted security use cases. Their offerings deliver controlled attack simulations, adversary engagement, and detailed forensic intelligence. These companies focus on affordability, ease of deployment, and strong operational insights.
Top Key Players in the Market
- Attivo Networks
- TrapX Security
- Illusive Networks
- Smokescreen Technologies
- Acalvio Technologies
- Cymmetria
- Guardicore
- Allure Security
- Fidelis Cybersecurity
- Rapid7
- LogRhythm
- CounterCraft
- CyberTrap
- Others
Future Outlook
The threat deception platform market is experiencing rapid growth as cybersecurity threats become more advanced and frequent. Organizations across industries are adopting these platforms to proactively detect, mislead, and analyze cyber attackers using decoys, traps, and AI-driven analytics.
The increasing complexities of digital transformation, cloud adoption, IoT proliferation, and stringent regulatory requirements are fueling demand. North America leads in market share, while Asia-Pacific is expected to see the highest growth due to expanding digital infrastructures and rising cybercrime. The shift toward zero-trust security architectures further expands opportunities for threat deception technologies.
Opportunities lie in
- Integration of AI and machine learning for enhanced threat detection and adaptive deception strategies.
- Growing adoption in high-risk sectors such as BFSI, healthcare, government, and defense requiring robust cybersecurity.
- Expansion in SMEs with cloud-based, subscription-model platforms lowering entry barriers.
- Integration with broader threat intelligence and SIEM systems for comprehensive cyber defense.
- Government initiatives promoting national cybersecurity infrastructure encourage investments in deception technologies.
Recent Developments
- July, 2025, Attivo Networks was acquired by SentinelOne, integrating its deception technology into SentinelOne’s Singularity XDR platform for broader automated threat detection and response.
- November, 2025, Attivo’s ThreatDefend platform expanded its presence on Microsoft Marketplace, highlighting its advanced machine learning and native integrations for faster incident response.
Report Scope
Report Features Description Market Value (2024) USD 2.1 Bn Forecast Revenue (2034) USD 8.7 Bn CAGR(2025-2034) 15.10% Base Year for Estimation 2024 Historic Period 2020-2023 Forecast Period 2025-2034 Report Coverage Revenue forecast, AI impact on Market trends, Share Insights, Company ranking, competitive landscape, Recent Developments, Market Dynamics and Emerging Trends Segments Covered By Component(Software, Services(Professional Services, Managed Services)) By Deployment Mode(Cloud-based, On-Premises) By Deception Stack(Network Deception, Endpoint Deception,Others) By Organization Size(Large Enterprises, Small and Medium-sized Enterprises (SMEs)) By End-User(Banking, Financial Services, and Insurance (BFSI), Others) Regional Analysis North America – US, Canada; Europe – Germany, France, The UK, Spain, Italy, Russia, Netherlands, Rest of Europe; Asia Pacific – China, Japan, South Korea, India, New Zealand, Singapore, Thailand, Vietnam, Rest of Latin America; Latin America – Brazil, Mexico, Rest of Latin America; Middle East & Africa – South Africa, Saudi Arabia, UAE, Rest of MEA Competitive Landscape Attivo Networks, TrapX Security, Illusive Networks, Smokescreen Technologies, Acalvio Technologies, Cymmetria, Guardicore, Allure Security, Fidelis Cybersecurity, Rapid7, LogRhythm, CounterCraft, CyberTrap, and others Customization Scope Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements. Purchase Options We have three license to opt for: Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited User and Printable PDF)  Threat Deception Platform MarketPublished date: Dec.2025add_shopping_cartBuy Now get_appDownload Sample
Threat Deception Platform MarketPublished date: Dec.2025add_shopping_cartBuy Now get_appDownload Sample -
-
- Attivo Networks
- TrapX Security
- Illusive Networks
- Smokescreen Technologies
- Acalvio Technologies
- Cymmetria
- Guardicore
- Allure Security
- Fidelis Cybersecurity
- Rapid7
- LogRhythm
- CounterCraft
- CyberTrap
- Others













