Global Hardware Security Modules Market Size, Share Analysis Report By Type (LAN Based, PCIE Based, USB Based, Cloud-Based HSMs), By Deployment (Cloud, On-premises), By Application (Payment Processing, Authentication, Public Key Infrastructure (PKI) Management, Database Encryption, IoT Security, Others), By End Use (BFSI, Government, Healthcare and Life Sciences, Retail and Consumer Products, Technology and Communication, Industrial and Manufacturing, Automotive, Others), Region and Companies - Industry Segment Outlook, Market Assessment, Competition Scenario, Trends and Forecast 2025-2034
- Published date: June 2025
- Report ID: 150038
- Number of Pages: 342
- Format:
-
keyboard_arrow_up
Quick Navigation
Report Overview
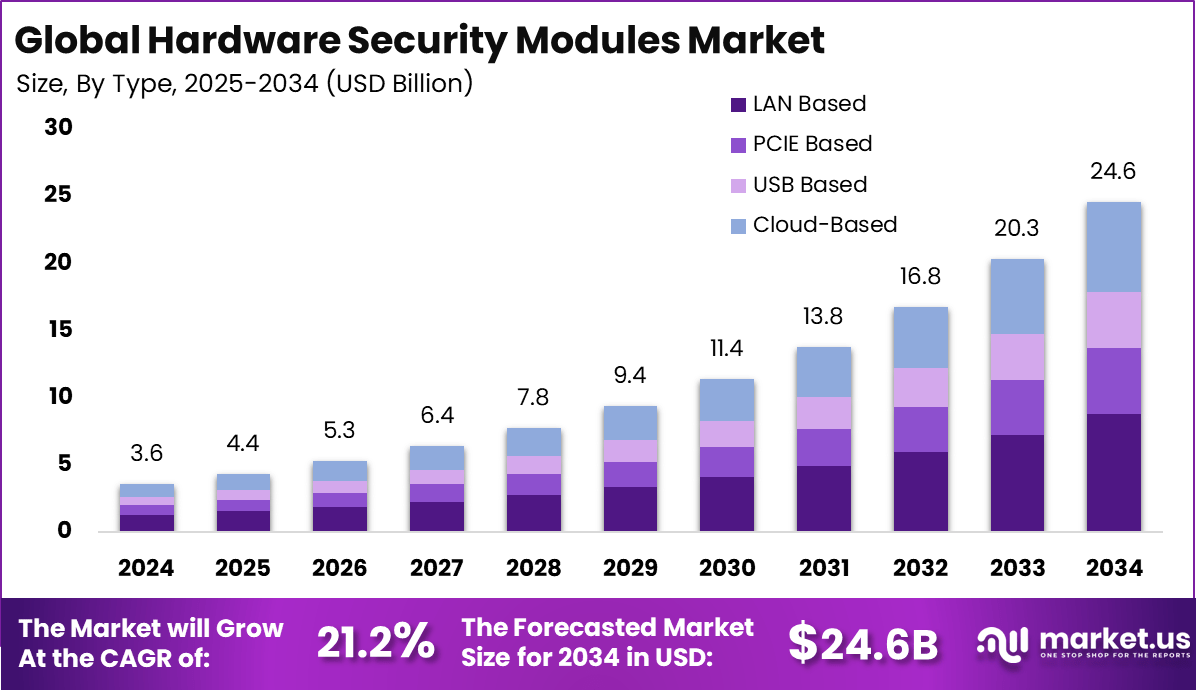
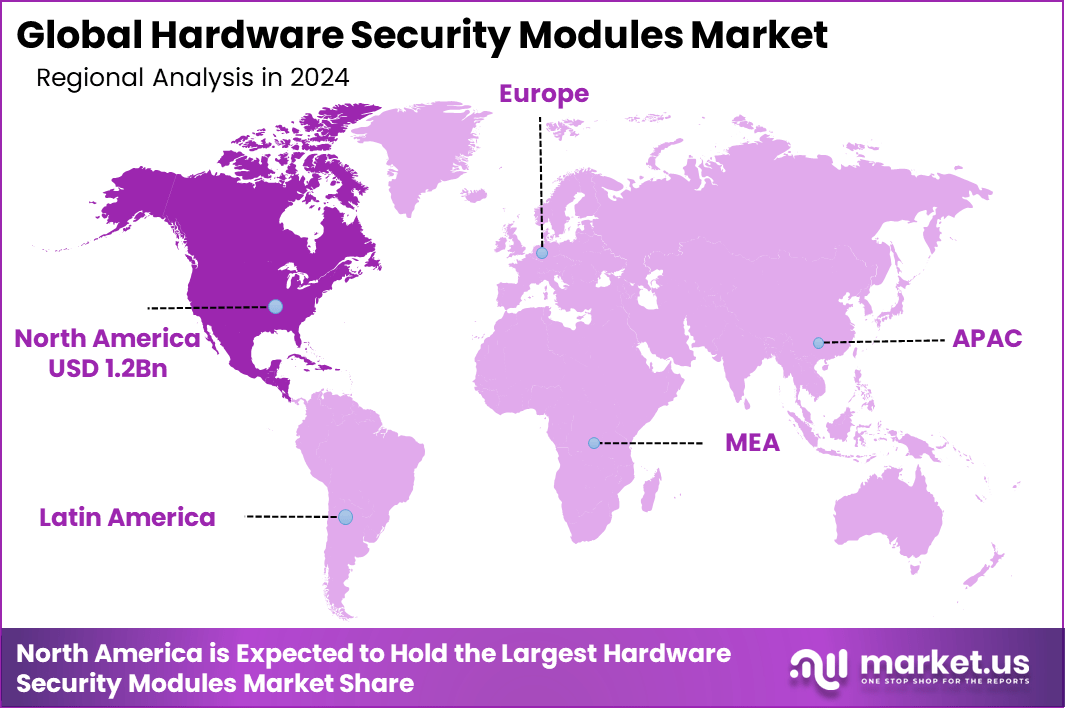
The Global Hardware Security Modules Market size is expected to be worth around USD 24.6 billion by 2034, from USD 3.6 billion in 2024, growing at a CAGR of 21.2% during the forecast period from 2025 to 2034. In 2024, North America held a dominant market position, capturing more than a 33.6% share, holding USD 1.2 billion in revenue.
The global Hardware Security Module market is experiencing significant growth, driven by the escalating need for robust cybersecurity solutions. Key factors propelling the adoption of HSMs include the surge in cyberattacks targeting sensitive data, the expansion of digital payment systems, and the necessity for compliance with data protection regulations such as GDPR and HIPAA.
Organizations are increasingly recognizing the importance of HSMs in securing cryptographic keys and ensuring the integrity of digital transactions. The demand for HSMs is particularly pronounced in sectors like banking, financial services, and government agencies, where data security is paramount.
For instance, In August 2024, Thales launched the Luna T-Series Tablet Hardware Security Module (HSM), a portable solution that delivers enterprise-grade cryptographic security with improved mobility. This innovation meets the rising demand for flexible, high-performance data protection across distributed environments.
Investments in the HSM market are being fueled by the growing emphasis on data security and regulatory compliance. Organizations are allocating resources to enhance their cybersecurity frameworks, with HSMs playing a critical role in protecting sensitive information. The market presents lucrative opportunities for vendors offering innovative HSM solutions that cater to the evolving security needs of various industries.
The World Economic Forum, in collaboration with Accenture, published the “Global Cybersecurity Outlook 2025” report. This comprehensive study provides insights into the evolving global cyber risk landscape, highlighting key trends, and the strategic priorities organizations must adopt to strengthen their cybersecurity posture in an increasingly digital world.
Key Takeaways
- In 2024, the global Hardware Security Modules (HSM) market saw LAN-based solutions leading with a 35.8% share, driven by demand for secure on-premises infrastructure in finance and government sectors.
- Cloud-based HSMs gained strong traction, holding 58.6% of the market, reflecting a shift toward remote key management and cryptographic operations in hybrid and multi-cloud environments.
- Among applications, payment processing accounted for 33.6%, underlining the critical role of HSMs in securing financial transactions and compliance with PCI DSS standards.
- The BFSI sector dominated usage with a 26.7% share, as financial institutions increasingly rely on HSMs to manage digital identities, encrypt transactions, and prevent fraud.
- Regionally, North America led the market with a 33.6% share, supported by early technology adoption and stringent regulatory mandates across banking and healthcare.
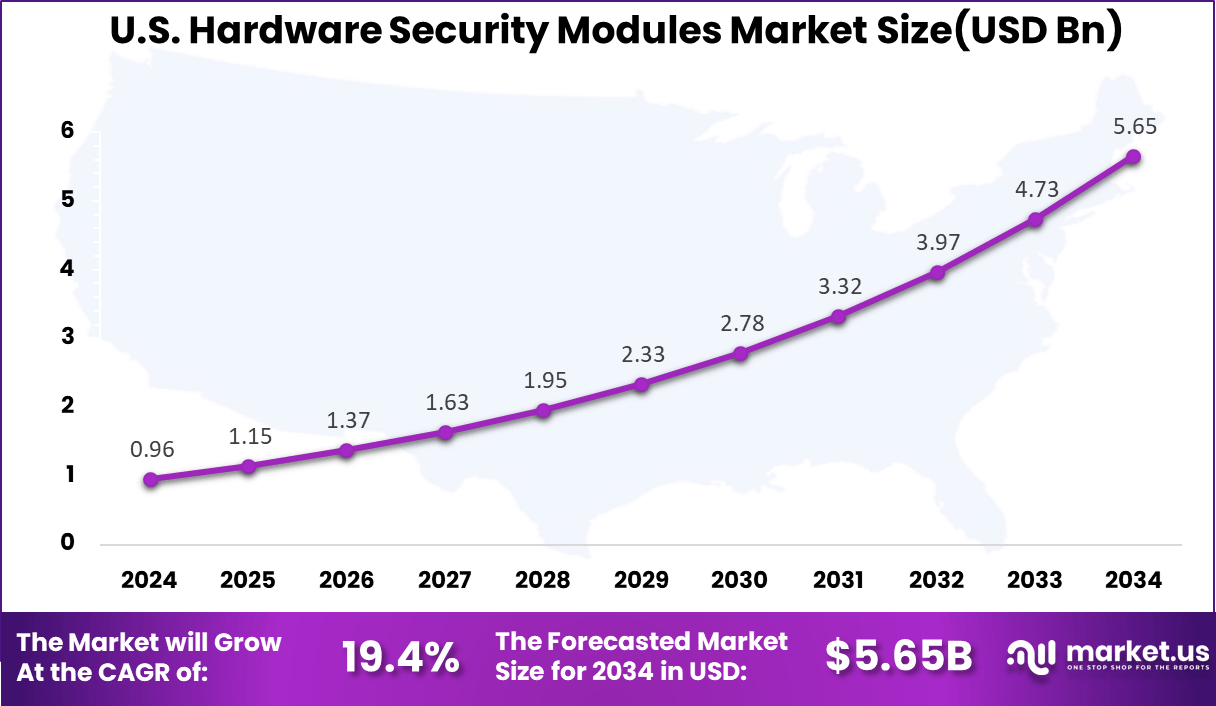
- In the U.S. alone, the HSM market was valued at USD 0.96 billion in 2024, growing at a strong CAGR of 19.4%, as enterprises continue to prioritize data protection amid rising cybersecurity threats.
Impact of AI on HSM
Artificial Intelligence (AI) is reshaping the landscape of Hardware Security Modules (HSMs), enhancing their capabilities to address the complexities of modern cybersecurity threats. Traditionally, HSMs have been instrumental in safeguarding cryptographic keys and performing secure encryption and decryption operations.
- Real-Time Threat Detection and Anomaly Analysis: AI empowers HSMs to analyze vast datasets, identifying anomalies and potential security breaches with heightened accuracy. Machine learning algorithms can detect unusual access patterns or cryptographic activities, facilitating immediate responses to mitigate risks.
- Automated Key Management: Managing cryptographic keys is a critical function of HSMs. AI streamlines this process by automating key generation, rotation, and revocation based on usage patterns and risk assessments. This automation minimizes human error, ensures timely updates, and maintains the integrity of cryptographic systems.
- Adaptive Encryption Protocols: AI enables HSMs to adapt encryption protocols dynamically, optimizing performance based on environmental factors such as server load and network conditions. This adaptability ensures that encryption processes remain efficient without compromising security, particularly in real-time applications like financial transactions and secure communications.
- Enhanced Authentication Mechanisms: Incorporating AI into HSMs enhances authentication processes through the use of biometric data and behavioral analytics. AI can facilitate multi-factor authentication methods, including facial recognition and fingerprint scanning, and adjust access controls based on contextual factors like user behavior and location.
- Predictive Maintenance and Health Monitoring: AI contributes to the longevity and reliability of HSMs by enabling predictive maintenance. By continuously monitoring performance metrics such as power consumption and response times, AI can predict potential failures, allowing for timely maintenance and reducing the risk of unexpected downtime.
US Market Expansion
The market for Hardware Security Modules within the U.S. is growing tremendously and is currently valued at USD 0.96 billion, the market has a projected CAGR of 19.4%. The U.S. Hardware Security Modules (HSM) market is experiencing rapid growth driven by escalating cyber threats and stringent regulatory requirements across industries such as finance, healthcare, and government.
For instance, In November 2024, Microsoft introduced a new range of in-house chips aimed at improving performance and security within its cloud and enterprise platforms in the U.S. These custom-built processors integrate advanced hardware-level security features, including secure key management and cryptographic support.
In 2024, North America held a dominant market position, capturing more than 33.6% share of the global Hardware Security Modules (HSM) market, with revenue exceeding USD 1.2 billion. This regional leadership is primarily attributed to the strong presence of major cloud service providers, digital payment networks, and cybersecurity vendors across the United States and Canada.
The region’s early adoption of encryption technologies in banking, defense, and healthcare has significantly driven the demand for HSMs, especially among government institutions and financial enterprises seeking FIPS 140-2 validated hardware for cryptographic key protection. The market strength in North America has also been fueled by increasing regulatory pressure for data security and privacy compliance.
Moreover, the rising frequency of ransomware and identity-based cyberattacks in this region has led organizations to prioritize hardware-based encryption over software-only solutions. The rapid growth of cloud-native HSM-as-a-service offerings by companies like AWS, IBM, and Microsoft further reinforces North America’s leadership by offering scalable, compliant cryptographic operations to both SMEs and large corporations.
In April 2024, X-Phy Inc., a prominent hardware cybersecurity company, appointed a new U.S. General Manager to boost its operations in North America. This strategic move highlights the firm’s focus on capturing growing demand for advanced hardware security amid rising cybersecurity investments and stricter regulatory requirements across sectors.
Type Analysis
In 2024, the LAN-based segment secured a leading position in the global hardware security modules (HSM) market, accounting for more than 35.8% of the total market share. This dominance is attributed to the segment’s robust network integration capabilities, which are crucial for organizations requiring centralized and secure management of cryptographic keys across their infrastructure.
The preference for LAN-based HSMs is driven by their ability to offer high-speed, low-latency cryptographic operations within a secured local network environment. This is particularly beneficial for sectors such as banking, financial services, and government, where data sensitivity and compliance with stringent security standards are paramount.
The centralized deployment model of LAN-based HSMs facilitates streamlined key management and simplifies adherence to regulatory requirements like PCI DSS and GDPR. Furthermore, the scalability and reliability of LAN-based HSMs make them suitable for enterprises with extensive IT infrastructures. Their integration into existing network systems allows for efficient handling of large volumes of cryptographic transactions, enhancing overall operational security.
For instance, In February 2025, Quantum Dice and Thales partnered to launch a LAN-based Hardware Security Module featuring integrated Quantum Random Number Generation (QRNG) technology. This solution enhances real-time security verification by offering advanced cryptographic key generation and robust tamper resistance within enterprise environments.
Deployment Analysis
In 2024, the cloud-based segment held a dominant position in the global hardware security modules (HSM) market, capturing more than a 58.6% share. This leadership is attributed to the increasing adoption of cloud computing and the demand for scalable, cost-effective security solutions.
Cloud-based HSMs offer organizations the flexibility to manage cryptographic keys and security processes without significant upfront investments in hardware. This model supports dynamic scaling to meet varying demands, enabling businesses to leverage robust security measures in the cloud while maintaining compliance with regulatory requirements.
The growth of the cloud-based HSM segment is further driven by the proliferation of digital transactions and the rise of cryptocurrencies, which necessitate secure cryptographic operations. Cloud-based HSMs provide a secure environment for key management and cryptographic processing within the cloud infrastructure, ensuring compliance with regulatory standards and safeguarding against cyber threats.
Moreover, the integration of artificial intelligence (AI) and machine learning (ML) technologies into cloud-based HSMs enhances their capabilities in predictive threat prevention and adaptive authentication mechanisms. AI-powered adaptive authentication systems improve user verification processes, making them more user-friendly and secure.
For instance, in August 2023, Thales launched a cloud-based Payment Hardware Security Module (HSM) service aimed at accelerating the adoption of cloud payments infrastructure. This service provides scalable, secure cryptographic key management tailored for payment processing environments, enabling financial institutions to transition to cloud-native architectures without compromising on security or compliance.
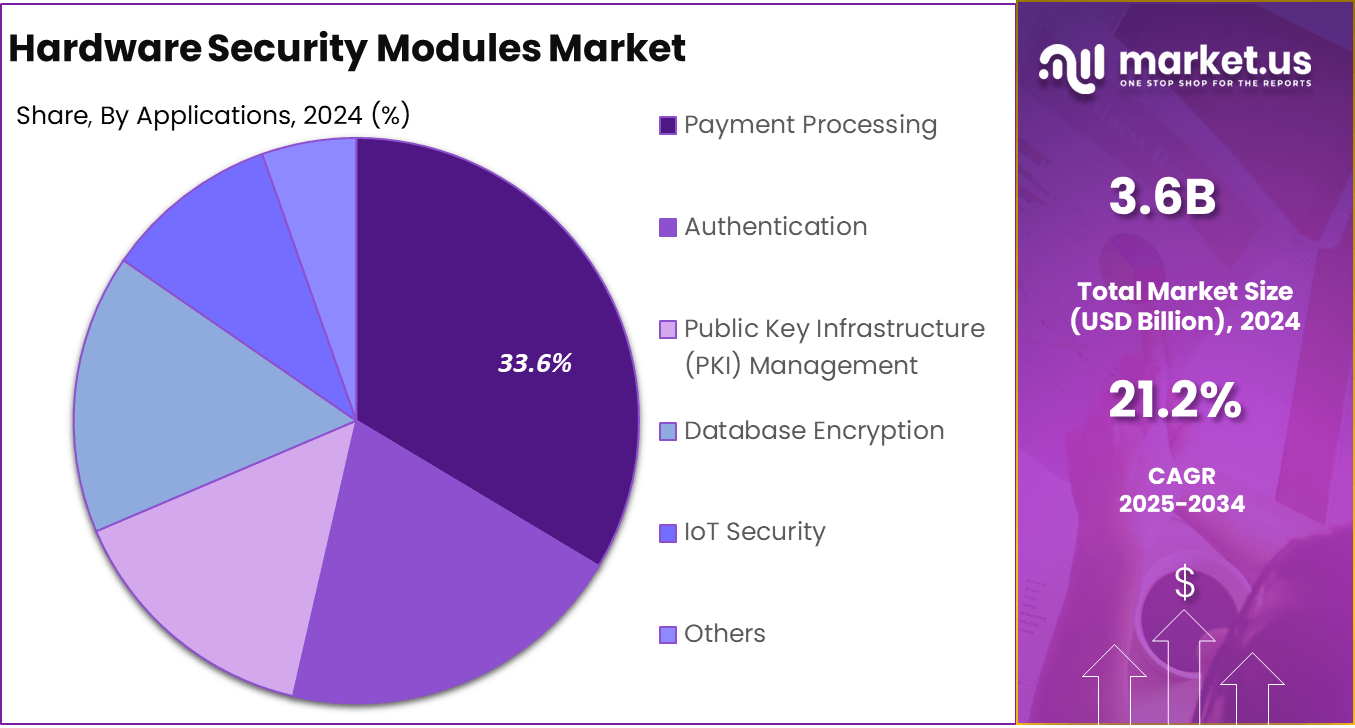
Application Analysis
In 2024, the payment processing segment held a dominant position in the global hardware security modules (HSM) market, capturing more than a 33.6% share. This leadership is attributed to the increasing volume of digital transactions and the stringent regulatory requirements that mandate secure handling of payment data.
Financial institutions and payment service providers rely on HSMs to ensure the confidentiality and integrity of sensitive information, complying with standards such as the Payment Card Industry Data Security Standard (PCI DSS). The robust encryption and key management capabilities of HSMs are essential for protecting against fraud and cyber threats in the payment ecosystem.
For instance, in October 2024, Jisa Softech officially launched the first Made-in-India Payment Hardware Security Module (HSM). This domestic innovation addresses the growing demand for secure, compliant cryptographic solutions tailored to local payment processing needs. By reducing reliance on foreign technology, the product supports India’s data sovereignty initiatives while enabling financial institutions to enhance transaction security.
The growth of the payment processing segment is further driven by the proliferation of e-commerce, mobile payments, and contactless transactions. As consumers increasingly adopt digital payment methods, the demand for secure and efficient transaction processing systems has surged. HSMs provide the necessary cryptographic functions to support these systems, including secure PIN processing, card issuance, and transaction authentication.
End Use Analysis
In 2024, the Banking, Financial Services, and Insurance (BFSI) sector held a dominant position in the global hardware security modules (HSM) market, capturing more than a 26.7% share. This leadership is attributed to the sector’s stringent requirements for data security and regulatory compliance.
HSMs provide robust encryption, secure key management, and authentication mechanisms essential for safeguarding transactions, customer information, and financial records. The adoption of HSMs in the BFSI sector is driven by the need to protect sensitive financial data and ensure compliance with standards such as the Payment Card Industry Data Security Standard (PCI DSS) and the General Data Protection Regulation (GDPR).
For instance, in October 2024, Ripple launched a bank-grade crypto custody solution targeting the $16 trillion tokenization market, underscoring the growing demand for advanced hardware security in the BFSI sector. This solution leverages Hardware Security Modules (HSMs) to provide secure cryptographic key management critical for safeguarding digital assets and ensuring regulatory compliance.
As financial institutions expand their digital services, the demand for secure and efficient transaction processing systems has surged. HSMs play a critical role in this ecosystem by providing the necessary cryptographic functions to support these systems, including secure PIN processing, card issuance, and transaction authentication.
Key Market Segments
By Type
- LAN Based
- PCIE Based
- USB Based
- Cloud-Based HSMs
By Deployment
- Cloud
- On-premises
By Application
- Payment Processing
- Authentication
- Public Key Infrastructure (PKI) Management
- Database Encryption
- IoT Security
- Others
By End Use
- BFSI
- Government
- Healthcare and Life Sciences
- Retail and Consumer Products
- Technology and Communication
- Industrial and Manufacturing
- Automotive
- Others
Key Regions and Countries
- North America
- US
- Canada
- Europe
- Germany
- France
- The UK
- Spain
- Italy
- Russia
- Netherlands
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- India
- Australia
- Singapore
- Thailand
- Vietnam
- Rest of APAC
- Latin America
- Brazil
- Mexico
- Rest of Latin America
- Middle East & Africa
- South Africa
- Saudi Arabia
- UAE
- Rest of MEA
Emerging Trends
The Hardware Security Module (HSM) market is undergoing significant transformation, driven by the escalating demand for advanced cryptographic solutions. A notable trend is the shift towards cloud-native HSMs, enabling organizations to manage cryptographic keys across diverse cloud environments without the need for physical hardware. This evolution offers scalability and flexibility, aligning with modern IT infrastructures.
Another emerging trend is the integration of post-quantum cryptography (PQC) into HSMs. With the advent of quantum computing, traditional encryption methods face potential obsolescence. Incorporating PQC ensures that cryptographic systems remain secure against future quantum threats, safeguarding sensitive data in the long term.
For instance, in May 2025, Axiado and GIGABYTE jointly showcased an advanced AI-driven hardware platform at Computex 2025, highlighting innovations in security and dynamic thermal management. This demonstration underscored the increasing convergence of artificial intelligence and hardware security, emphasizing the role of AI in enhancing real-time threat detection and system performance optimization.
Business Benefits
Implementing HSMs offers businesses a robust mechanism to protect sensitive data. By securely generating, storing, and managing cryptographic keys within tamper-resistant hardware, HSMs significantly reduce the risk of data breaches and unauthorized access. This level of security is essential for maintaining customer trust and complying with data protection regulations.
Moreover, HSMs enhance operational efficiency by automating cryptographic processes. Tasks such as digital signing, authentication, and encryption are streamlined, reducing the computational burden on primary systems. This not only improves system performance but also allows IT teams to focus on strategic initiatives, thereby contributing to overall business agility.
Drivers
Rising Cybersecurity Threats and Data Breaches
The increasing sophistication and frequency of cyberattacks globally are driving demand for robust cryptographic solutions. Hardware Security Modules (HSMs) deliver critical secure key management and encryption functionalities that support data protection strategies.
Consequently, they have become crucial for sectors such as banking, government agencies, and cloud service providers, where safeguarding sensitive information is vital to operational resilience and regulatory compliance.
For instance, in October 2023, the ACE Hardware data breach exposed critical vulnerabilities in the company’s IT systems, resulting in the compromise of sensitive customer data for over 7,000 individuals. This incident underscored the urgent need for stronger hardware-based security measures, such as HSMs, particularly within retail and other data-sensitive industries, to safeguard cryptographic keys and prevent unauthorized data access.
Restraint
High Cost of Implementation and Maintenance
Hardware Security module deployments represent considerable capital expenditure, encompassing not only the initial procurement but also ongoing operational and maintenance costs. This financial barrier constrains adoption, particularly among small and medium-sized enterprises (SMEs), which may lack the budgetary flexibility to invest in dedicated hardware security infrastructure despite growing security imperatives.
As noted by Yubico, the total cost of ownership for Hardware Security Modules (HSMs) extends beyond the initial purchase, encompassing integration with IT systems, ongoing firmware updates, maintenance, and compliance audits. These cumulative expenses can rise sharply, especially when scaling infrastructure or adapting to new security regulations.
Opportunities
Cloud-Based HSM Solutions
The increasing shift to cloud solution adoption is catalyzing demand for cloud-native HSM offerings. These solutions mitigate traditional cost barriers by eliminating heavy upfront investments and enable organizations to adopt security architectures that are both scalable and flexible.
These solutions enable organizations to securely manage cryptographic keys within cloud and hybrid environments, unlocking growth potential in emerging markets and sectors undergoing digital transformation.
For instance, In April 2025, Utimaco introduced its Payment HSM-as-a-Service (HSMAAS) on IBM Cloud, delivering secure and compliant cryptographic key management as a fully managed cloud solution. Targeted at financial institutions and payment providers, this launch aims to improve data protection, regulatory compliance, and operational agility by utilizing IBM Cloud’s robust infrastructure.
Challenges
Compliance with Stringent Security Standards
Hardware Security Modules (HSMs) operate in highly regulated environments where adherence to strict security standards is mandatory. Ensuring compliance with these evolving standards poses a significant challenge for organizations and vendors alike.
This is particularly critical as HSMs serve as the cornerstone for cryptographic key management, protecting sensitive data in industries such as finance, healthcare, and government. The compliance process demands rigorous design, testing, and certification efforts, which can prolong product development cycles and increase costs.
For instance, FIPS 140-2 (Federal Information Processing Standard Publication 140-2) is a U.S. government standard that defines the security requirements for cryptographic modules, including HSMs. HSMs compliant with FIPS 140-2 undergo rigorous testing and validation to ensure they meet stringent security criteria such as physical tamper resistance, cryptographic key management, and secure operational controls.
Key Player Analysis
The Hardware Security Modules (HSM) market is witnessing a surge in strategic initiatives aimed at enhancing technological capabilities, expanding global reach, and addressing evolving cybersecurity needs. Companies across this space are actively engaging in new product development, strategic partnerships, and targeted collaborations to gain a competitive edge and cater to regulatory compliance requirements across industries.
In 2024, Microsoft introduced the Azure Integrated Hardware Security Module (HSM), a custom security chip designed to enhance data protection across its cloud infrastructure. This HSM is being integrated into all new Azure servers starting in 2025, aiming to bolster cryptographic key management and secure sensitive data.
In early 2025, IBM completed the acquisition of HashiCorp, a company specializing in infrastructure automation and security. This strategic move is expected to enhance IBM’s capabilities in managing and securing hybrid cloud environments. By integrating HashiCorp’s solutions, IBM aims to offer comprehensive security features, including robust HSM services, to its enterprise clients.
In May 2025, Box announced the launch of its new AI platform, introducing powerful AI agents to enterprise content management. These AI agents are designed to enhance search capabilities, facilitate deep research, and improve data extraction processes. The platform also includes an AI agent for Microsoft 365 Copilot, enabling seamless interactions across third-party platforms.
Top Key Players Covered
- Alfresco Software, Inc.
- Box, Inc.
- DocuWare Corporation
- Hyland Software, Inc.
- International Business Machines Corporation
- Laserfiche
- M-Files Corporation
- Microsoft
- OpenText Corporation
- Oracle
- Others
Recent Developments
- In December 2024, Futurex partnered with Vietnam’s leading digital bank, Cake, to implement cloud-based payment HSM technology, leading to the country’s first fully cloud-based card management system. Operating via Visa Cloud Connect and secured by Futurex’s HSMs, the system marks a significant advancement in Vietnam’s digital payment infrastructure.
- In October 2024, Eviden introduced PQC HSMaaS, a post-quantum cryptography HSM-as-a-Service, distinguished by its “reinforced qualification” from ANSSI. Delivered under the Trustway Proteccio brand, this sovereign solution ensures top-tier cryptographic protection for critical business operations.
- Additionally, in May 2024, Utimaco and ShardSecure joined forces to deliver a comprehensive data protection solution, integrating Utimaco’s HSMs to secure encryption keys for unstructured data safeguarded by ShardSecure, thus offering robust encryption and threat resilience across data types.
Report Scope
Report Features Description Market Value (2024) USD 3.6 Bn Forecast Revenue (2034) USD 24.6 Bn CAGR (2025-2034) 21.2% Base Year for Estimation 2024 Historic Period 2020-2023 Forecast Period 2025-2034 Report Coverage Revenue forecast, AI impact on market trends, Share Insights, Company ranking, competitive landscape, Recent Developments, Market Dynamics and Emerging Trends Segments Covered By Type (LAN Based, PCIE Based, USB Based, Cloud-Based HSMs), By Deployment (Cloud, On-premises), By Application (Payment Processing, Authentication, Public Key Infrastructure (PKI) Management, Database Encryption, IoT Security, Others), By End Use (BFSI, Government, Healthcare and Life Sciences, Retail and Consumer Products, Technology and Communication, Industrial and Manufacturing, Automotive, Others) Regional Analysis North America – US, Canada; Europe – Germany, France, The UK, Spain, Italy, Russia, Netherlands, Rest of Europe; Asia Pacific – China, Japan, South Korea, India, New Zealand, Singapore, Thailand, Vietnam, Rest of APAC; Latin America – Brazil, Mexico, Rest of Latin America; Middle East & Africa – South Africa, Saudi Arabia, UAE, Rest of MEA Competitive Landscape Alfresco Software, Inc., Box, Inc., DocuWare Corporation, Hyland Software, Inc., International Business Machines Corporation, Laserfiche, M-Files Corporation, Microsoft, OpenText Corporation, Oracle, Others Customization Scope Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements. Purchase Options We have three license to opt for: Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited User and Printable PDF)  Hardware Security Modules MarketPublished date: June 2025add_shopping_cartBuy Now get_appDownload Sample
Hardware Security Modules MarketPublished date: June 2025add_shopping_cartBuy Now get_appDownload Sample -
-
- Alfresco Software, Inc.
- Box, Inc.
- DocuWare Corporation
- Hyland Software, Inc.
- International Business Machines Corporation
- Laserfiche
- M-Files Corporation
- Microsoft
- OpenText Corporation
- Oracle
- Others













