Global Workload Identity Security Market Size, Share Report Analysis By Component (Solutions, Services), By Deployment Mode (On-Premises, Cloud), By Organization Size (Large Enterprises, Small and Medium Enterprises), By Application (DevOps Security, Cloud Workload Protection, Compliance Management, Access Management, Others), By End-User (BFSI, Healthcare, IT and Telecommunications, Retail, Government, Manufacturing, Others), By Regional Analysis, Global Trends and Opportunity, Future Outlook By 2025-2034
- Published date: Dec. 2025
- Report ID: 170301
- Number of Pages: 392
- Format:
-
keyboard_arrow_up
Quick Navigation
- Report Overview
- Key Takeaway
- Key Statistics
- Role of Generative AI
- U.S. Market Size
- Component Analysis
- Deployment Mode Analysis
- Organization Size Analysis
- Application Analysis
- End-User Analysis
- Emerging Trends
- Growth Factors
- Key Market Segments
- Driver Analysis
- Restraint Analysis
- Opportunity Analysis
- Key Players Analysis
- Recent Developments
- Report Scope
Report Overview
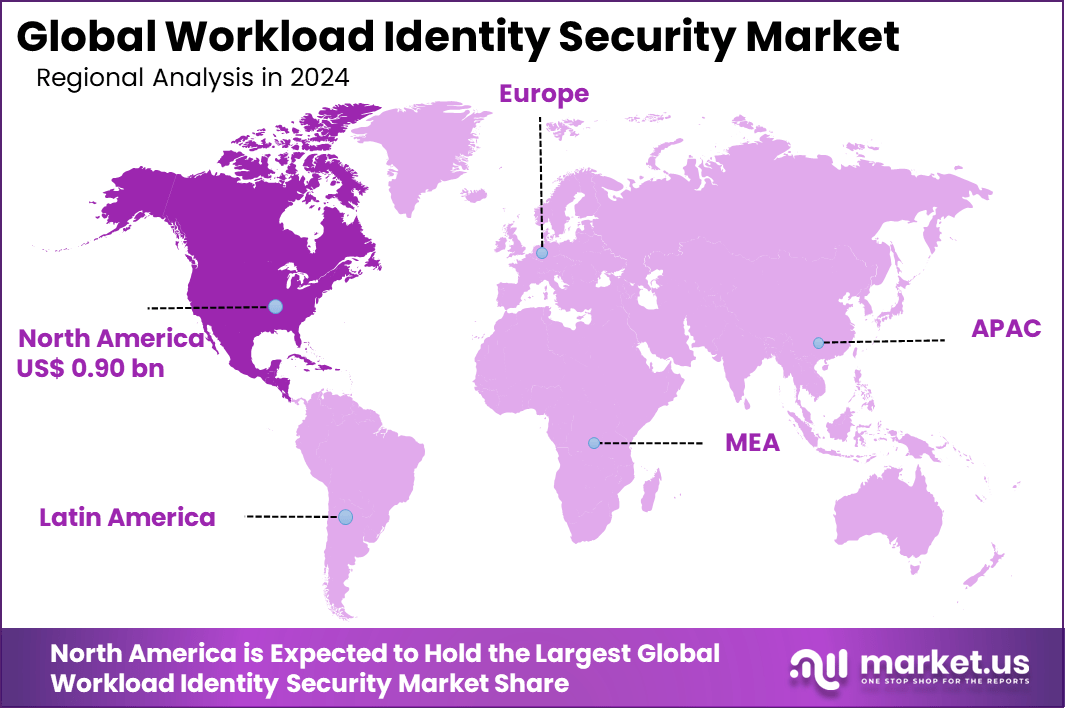
The Global Workload Identity Security Market size is expected to be worth around USD 27.31 billion by 2034, from USD 2.35 billion in 2024, growing at a CAGR of 27.8% during the forecast period from 2025 to 2034. North America held a dominant market position, capturing more than a 38.6% share, holding USD 0.90 billion in revenue.
The workload identity security market consists of products and practices that protect digital identities assigned to workloads, which are non-human entities such as applications, services, containers, or automated processes. These identities are used to authenticate and authorize access to systems, resources, and data in cloud-native and hybrid IT environments.
Workload identities differ from traditional human user identities in that they are dynamic, short-lived, and often created at runtime as part of automated workflows. This form of identity security is essential for maintaining secure access controls in modern distributed applications and systems where human-centric identity controls are insufficient.
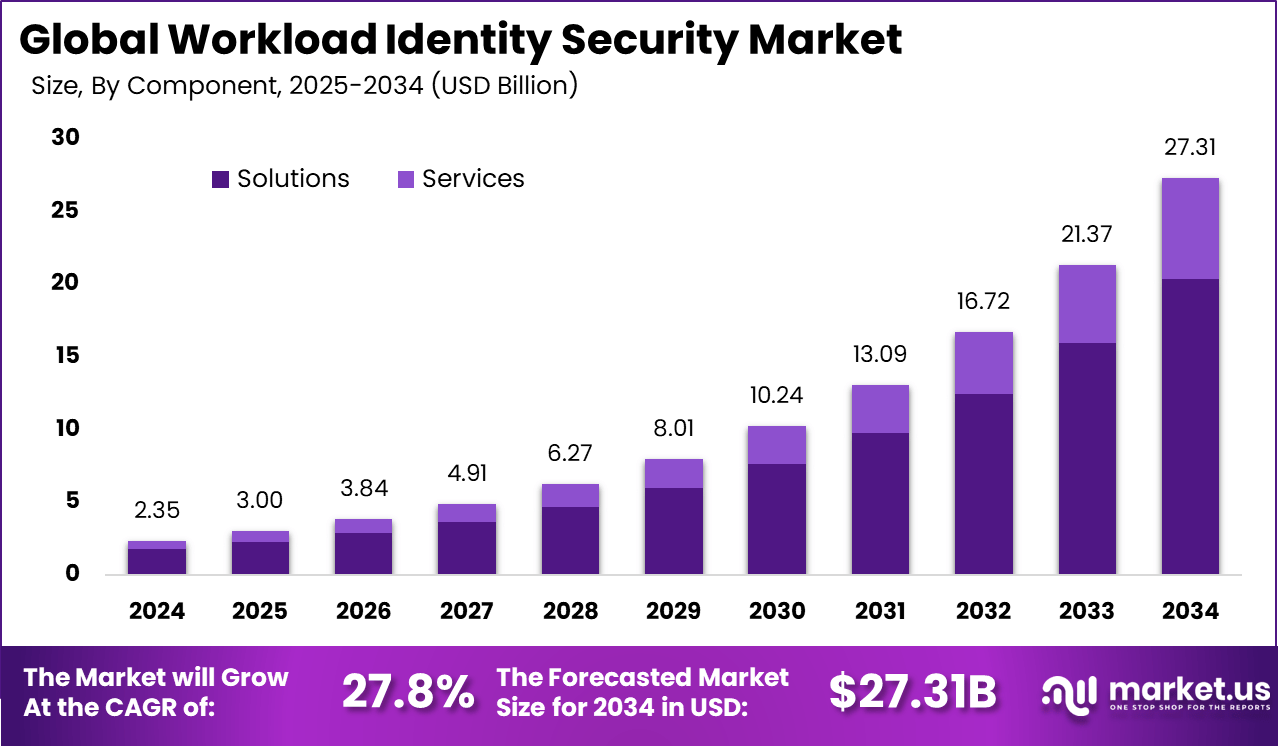
The market for Workload Identity Security is driven by rapid cloud adoption and rising cyber threats. Firms shift to multi-cloud setups, creating more machine identities that need tight controls. Tools like federation cut key risks and ease hybrid access. Digital shifts demand automated checks against breaches. Regulations push secure workload management too.
For instance, in September 2025, Microsoft Azure Entra ID got a boost via Aembit’s support for Workload Identity Federation, letting apps from other clouds or on-prem hit Azure resources without static secrets. This cross-cloud federation pairs well with verification and conditional access, making multi-environment security less of a nightmare.
Key Takeaway
- Solutions dominated with 74.7% in 2024, showing strong enterprise preference for integrated workload identity security platforms over standalone tools.
- On-premises deployment accounted for 58.4%, reflecting continued demand for direct control and compliance in sensitive security environments.
- Large enterprises held 70.3%, driven by complex cloud and hybrid infrastructures that require strict identity governance.
- Cloud workload protection captured 37.2%, highlighting rising focus on securing non-human identities across containers, microservices, and virtual machines.
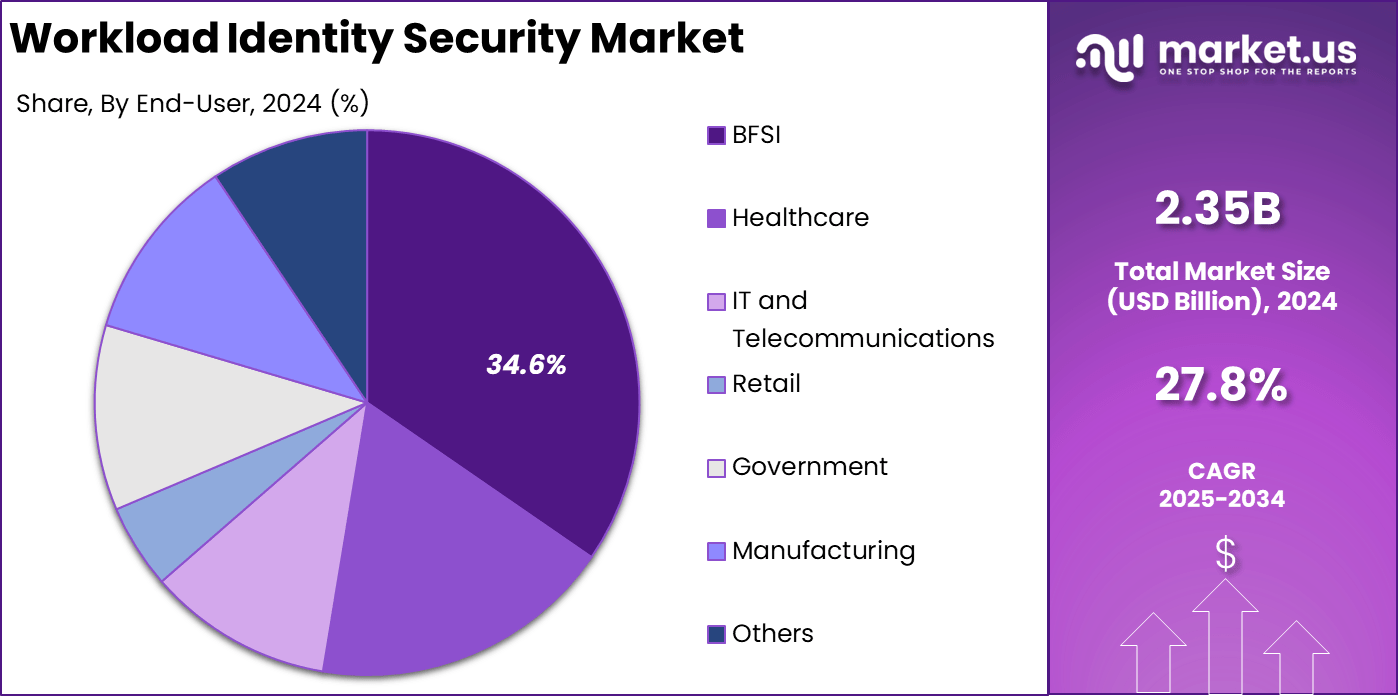
- The BFSI sector led with 34.6%, supported by high regulatory pressure and increasing cloud workload exposure.
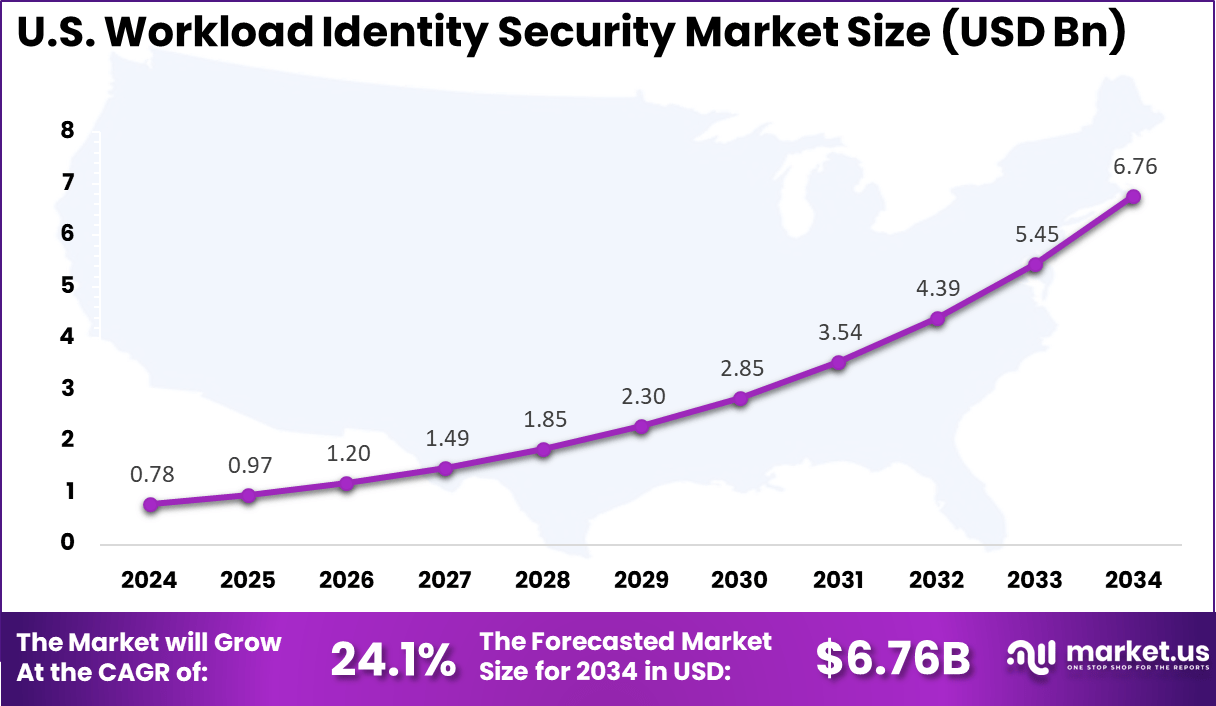
- The U.S. market reached USD 0.78 billion in 2024 and is growing at a strong 24.1% CAGR, driven by zero-trust adoption and cloud security modernization.
- North America held more than 38.6%, backed by advanced cybersecurity frameworks, early adoption of identity-first security models, and strong enterprise spending.
Key Statistics
- Machine identities now outnumber human users by more than 80:1, making non-human identities the largest and fastest-growing attack surface in modern enterprises.
- Around 8%-9.5% of scanned Docker images in 2023–2024 contained exposed API keys or credentials, highlighting widespread secret sprawl across cloud workloads.
- About 63% of cloud security breaches involve compromised machine identities, showing that identity mismanagement is a primary breach driver.
- Over-permissioning remains common, with many workload identities granted excessive privileges, creating high-risk super identities that expand attack surfaces significantly.
Role of Generative AI
Generative AI changes how workload identity security works by spotting threats faster through pattern analysis. It scans machine access in real time and flags odd behavior before damage happens. 41% of teams struggle with security gaps when rolling out these AI tools in their systems. This pushes for tighter controls around automated processes that handle sensitive data flows.
The tech also learns from past incidents to predict risks better. Overall, it makes defenses more proactive instead of just reactive. AI steps in for anomaly checks on non-human accounts like services and bots. With more AI agents in play, security covers a wider range of digital actors.
72% of security groups now lean on GenAI to fight off growing attacks on identities. This shift helps manage the flood of machine logins without overwhelming staff. Teams feel the pressure to integrate it smoothly while keeping risks low. In short, GenAI turns complex monitoring into something more manageable day to day.
U.S. Market Size
The market for Workload Identity Security within the U.S. is growing tremendously and is currently valued at USD 0.78 billion, the market has a projected CAGR of 24.1%. The market is growing due to the rapid shift to cloud and hybrid environments, where non-human identities like apps and services outnumber human users.
Firms face rising threats from stolen machine credentials, pushing demand for tools that enforce short-lived access and real-time monitoring. Regulations in finance and healthcare add pressure for better controls, while AI-driven workloads need secure automation to scale without risks.
In November 2025, Microsoft upgraded its Entra Workload ID capabilities by adding location based conditional access, risk driven ID protection, and governance tools for managing non human identities. These enhancements strengthen just in time access control, threat detection, and automated reviews, reinforcing U.S. leadership in workload identity security across hybrid cloud environments.
In 2024, North America held a dominant market position in the Global Workload Identity Security Market, capturing more than a 38.6% share, holding USD 0.90 billion in revenue. This dominance is due to the region’s advanced cloud adoption and dense concentration of tech firms pushing non-human identity tools.
Early movers in hyperscale data centers face constant threats to machine credentials, driving investments in real-time protection. Strict rules in BFSI and healthcare force quick upgrades, while hybrid setups demand seamless controls across on-premises and cloud workloads.
For instance, in May 2025, Saviynt expanded its Identity Cloud platform to protect all identities, including non-human identities (NHIs) like workloads, bots, and credentials, offering discovery, security posture analysis, and visualization tools. This converged solution eliminates blind spots in cloud-hybrid environments, showcasing North American innovation in comprehensive workload identity security.
Component Analysis
The solutions segment leads with 74.7%, showing that most workload identity security adoption is centered on software-based security platforms. These solutions help organizations manage identities for workloads such as applications, containers, and virtual machines across on-premises and cloud environments.
Demand is driven by the need to reduce identity-based attack risks and improve visibility across machine identities. Solution platforms support automated credential management, policy enforcement, and continuous monitoring, which strengthens security posture across modern IT systems.
For Instance, in October 2025, CyberArk expanded its machine identity security portfolio with advanced discovery tools. These updates help teams find and manage non-human identities across cloud and on-premises setups. Security leads now get better context on risks from workloads like apps and services, making it easier to enforce controls without blind spots.
Deployment Mode Analysis
In 2024, On-premises deployment accounts for 58.4%, reflecting strong preference among organizations handling sensitive data. Enterprises rely on on-site systems to maintain tighter control over identity data and security policies.
This deployment mode is favored in environments with strict internal security rules and regulatory requirements. On-premises systems also support integration with legacy infrastructure, which remains common across large organizations.
For instance, in September 2025, HashiCorp updated Vault and Boundary for better on-premises credential handling. Admins set dynamic secrets that rotate automatically, reducing overprovisioned access in legacy environments. Teams gain control without exposing keys during daily operations.
Organization Size Analysis
In 2024, Large enterprises represent 70.3% of market adoption, highlighting their higher exposure to identity-related security risks. These organizations operate complex IT environments with thousands of workloads that require consistent identity control.
Their adoption is supported by larger security budgets and advanced risk management strategies. Large enterprises also face higher regulatory pressure, which increases the need for strong workload identity governance.
For Instance, in September 2025, Ping Identity launched an AI-driven trust framework for big firms. It secures AI agents and streamlines access across massive networks with governance workflows. Large enterprises cut oversight gaps in sprawling IT setups this way.
Application Analysis
In 2024, Cloud workload protection holds 37.2%, making it the leading application area. Organizations use workload identity security to protect cloud-native applications, containers, and microservices from unauthorized access.
Growth in this segment is linked to expanding cloud adoption and distributed application architectures. Identity-based protection improves access control and reduces reliance on static credentials in dynamic cloud environments.
For Instance, in November 2025, Google Cloud enhanced Workload Identity Federation for multi-cloud protection. On-premises and cloud workloads authenticate without service account keys using OIDC. This shields running instances from credential theft in dynamic apps.
End-User Analysis
In 2024, The BFSI segment held a dominant market position, capturing a 34.6% share of the Global Workload Identity Security Market. Banks and financial firms lead here due to the high stakes of handling transactions and customer data, where a single identity slip can lead to big losses. They use these tools to lock down APIs and automated processes that run nonstop.
Financial outfits prioritize this because regulations demand ironclad controls over every machine-to-machine link. Tools help verify workloads before granting access to payment systems or trading platforms. In fast-paced trading floors, they prevent fraud by watching for unusual patterns in automated trades.
For Instance, in September 2025, Okta introduced verifiable digital credentials to fight AI fraud in finance. Banks issue tamper-proof IDs for transactions, cutting onboarding friction while verifying workloads. BFSI gains trust in automated payment flows.
Emerging Trends
The workload identity security market is evolving rapidly as enterprises shift toward cloud native and hybrid environments where non human identities now outnumber human users. A key trend is the growing adoption of identity based security models that replace static secrets with short lived credentials and just in time access.
Organizations are increasingly applying zero trust principles to workloads, ensuring that every service, API, and application is continuously verified before accessing resources. Another notable trend is deeper integration of workload identity security with cloud platforms and DevSecOps pipelines, allowing security controls to be embedded early in application development and deployment processes.
AI driven threat detection is also becoming more prominent across workload identity security solutions. Advanced analytics are being used to monitor abnormal behavior of service accounts, containers, and machine identities in real time. At the same time, regulatory pressure around data access and auditability is pushing vendors to strengthen governance, visibility, and automated access reviews for non human identities.
Growth Factors
Market growth is primarily driven by the rapid expansion of cloud computing, microservices, and API based architectures, which significantly increase the number of machine identities that require protection. As enterprises adopt multi cloud and hybrid strategies, securing workload to workload communication becomes critical to prevent lateral movement and privilege misuse.
Rising incidents of credential theft, API abuse, and supply chain attacks further reinforce demand for stronger workload identity controls that reduce reliance on long lived secrets. Another major growth factor is enterprise focus on automation and operational efficiency. Organizations seek scalable security solutions that reduce manual identity management while maintaining compliance with internal and external regulations.
Increasing adoption of zero trust frameworks, combined with stricter data protection requirements across regions, continues to accelerate investment in workload identity security platforms. Together, these factors support sustained market expansion as digital infrastructure becomes more complex and interconnected.
Key Market Segments
By Component
- Solutions
- Services
By Deployment Mode
- On-Premises
- Cloud
By Organization Size
- Large Enterprises
- Small and Medium Enterprises
By Application
- DevOps Security
- Cloud Workload Protection
- Compliance Management
- Access Management
- Others
By End-User
- BFSI
- Healthcare
- IT and Telecommunications
- Retail
- Government
- Manufacturing
- Others
Regional Analysis and Coverage
- North America
- US
- Canada
- Europe
- Germany
- France
- The UK
- Spain
- Italy
- Russia
- Netherlands
- Rest of Europe
- Asia Pacific
- China
- Japan
- South Korea
- India
- Australia
- Singapore
- Thailand
- Vietnam
- Rest of Latin America
- Latin America
- Brazil
- Mexico
- Rest of Latin America
- Middle East & Africa
- South Africa
- Saudi Arabia
- UAE
- Rest of MEA
Driver Analysis
A primary driver of the workload identity security market is the shift toward cloud native and hybrid IT environments. As organizations migrate applications and workloads to the cloud, the number of identities used by services and workloads increases substantially. Protecting these identities and controlling their access across environments becomes essential for securing critical infrastructure and data.
A second driver is regulatory and compliance pressure. Many data protection and cybersecurity standards now require controls around identity and access management for all types of accounts, including non-human identities. Organizations adopt workload identity security solutions to demonstrate compliance and to reduce risk in audits.
Restraint Analysis
One restraint is the complexity of integrating workload identity security into existing systems. Many organizations operate legacy systems that were not designed with modern identity frameworks. Applying workload identity controls to older applications, services and infrastructure can require significant reworking of access models and credential management. This complexity may slow adoption, especially in large enterprises with varied technology stacks.
Another restraint is the shortage of skilled personnel who understand both identity security and modern application environments. Implementing, configuring and maintaining workload identity security requires deep knowledge of identity protocols, cloud architecture and application behaviour. A lack of trained staff can delay deployment and reduce the effectiveness of these solutions.
Opportunity Analysis
One opportunity lies in expanding support for multi cloud and hybrid environments. As organizations spread workloads across different cloud providers and on-premise data centres, workload identity security solutions that provide unified policy control and visibility across all these environments can attract strong interest.
Another opportunity is the integration of workload identity security with broader security operations. By combining identity signals with threat detection, vulnerability data and incident response processes, organizations can build a more holistic security posture. Vendors that offer such integrated capabilities may find greater demand from security teams seeking efficiency and broader protection.
Key Players Analysis
CyberArk, Microsoft, Okta, HashiCorp, and Ping Identity lead the workload identity security market with platforms that secure machine identities across cloud, containers, and microservices. Their solutions manage secrets, certificates, and access policies for non-human workloads. These companies focus on zero-trust enforcement, automation, and deep cloud-native integration.
IBM, Google Cloud, AWS, BeyondTrust, Delinea, One Identity, SailPoint, Oracle, and Akamai strengthen the market with identity governance, privileged access controls, and runtime security for workloads. Their platforms help enterprises reduce credential sprawl, enforce least-privilege access, and maintain compliance. These providers emphasize scalability, policy orchestration, and visibility across hybrid and multi-cloud environments.
Saviynt, JumpCloud, Auth0, Fugue, Sonrai Security, Ermetic, and other players broaden the market with specialized tools for cloud entitlement management and identity posture monitoring. Their offerings focus on misconfiguration detection, continuous assessment, and fast remediation. These companies support organizations seeking simpler deployment and real-time control over workload identities.
Top Key Players in the Market
- CyberArk
- Microsoft
- Okta
- HashiCorp
- Ping Identity
- IBM
- Google Cloud
- Amazon Web Services (AWS)
- BeyondTrust
- Delinea
- One Identity
- SailPoint
- Oracle
- Akamai Technologies
- Saviynt
- JumpCloud
- Auth0
- Fugue
- Sonrai Security
- Ermetic
- Others
Recent Developments
- In April 2025, CyberArk debuted its Secure Workload Access Solution, the first comprehensive tool for machine identities in hybrid clouds, blending unique workload IDs with secrets management. The Workload Identity Manager automates discovery for Kubernetes and enforces least privilege, closing big gaps in non-human access protection.
- In September 2025, Microsoft Azure Entra ID got a boost via Aembit’s support for Workload Identity Federation, letting apps from other clouds or on-prem hit Azure resources without static secrets. This cross-cloud federation pairs well with verification and conditional access, making multi-environment security less of a nightmare.
Report Scope
Report Features Description Market Value (2024) USD 2.3 Bn Forecast Revenue (2034) USD 27.3 Bn CAGR(2025-2034) 27.8% Base Year for Estimation 2024 Historic Period 2020-2023 Forecast Period 2025-2034 Report Coverage Revenue forecast, AI impact on Market trends, Share Insights, Company ranking, competitive landscape, Recent Developments, Market Dynamics and Emerging Trends Segments Covered By Component (Solutions, Services), By Deployment Mode (On-Premises, Cloud), By Organization Size (Large Enterprises, Small and Medium Enterprises), By Application (DevOps Security, Cloud Workload Protection, Compliance Management, Access Management, Others), By End-User (BFSI, Healthcare, IT and Telecommunications, Retail, Government, Manufacturing, Others) Regional Analysis North America – US, Canada; Europe – Germany, France, The UK, Spain, Italy, Russia, Netherlands, Rest of Europe; Asia Pacific – China, Japan, South Korea, India, New Zealand, Singapore, Thailand, Vietnam, Rest of Latin America; Latin America – Brazil, Mexico, Rest of Latin America; Middle East & Africa – South Africa, Saudi Arabia, UAE, Rest of MEA Competitive Landscape CyberArk, Microsoft, Okta, HashiCorp, Ping Identity, IBM, Google Cloud
Amazon Web Services (AWS), BeyondTrust, Delinea, One Identity, SailPoint, Oracle, Akamai Technologies, Saviynt, JumpCloud, Auth0, Fugue, Sonrai Security, Ermetic, OthersCustomization Scope Customization for segments, region/country-level will be provided. Moreover, additional customization can be done based on the requirements. Purchase Options We have three license to opt for: Single User License, Multi-User License (Up to 5 Users), Corporate Use License (Unlimited User and Printable PDF)  Workload Identity Security MarketPublished date: Dec. 2025add_shopping_cartBuy Now get_appDownload Sample
Workload Identity Security MarketPublished date: Dec. 2025add_shopping_cartBuy Now get_appDownload Sample -
-
- CyberArk
- Microsoft
- Okta
- HashiCorp
- Ping Identity
- IBM
- Google Cloud
- Amazon Web Services (AWS)
- BeyondTrust
- Delinea
- One Identity
- SailPoint
- Oracle
- Akamai Technologies
- Saviynt
- JumpCloud
- Auth0
- Fugue
- Sonrai Security
- Ermetic
- Others













